FCSC 2020 - Flag Checker (web)
Web - Flag Checker
The goal is to understand how this web app validate the input sent by the user. When I started this challenge, may be one hour after it release there was already a lot of resolution. This fact helped me to keep my ideas clear and simple.
When browsing, you just have a form. Let’s look inside the javascript code.
There is also a index.wasm associated, mmmmh very interesting I never reversed wasm before. It can be difficult as simple, it only depends on the code behind.
There are some webasm decompilers but none worked for this challenge, never mind it must be easy with all this validation ..
I went function call by function call until I found something interesting.
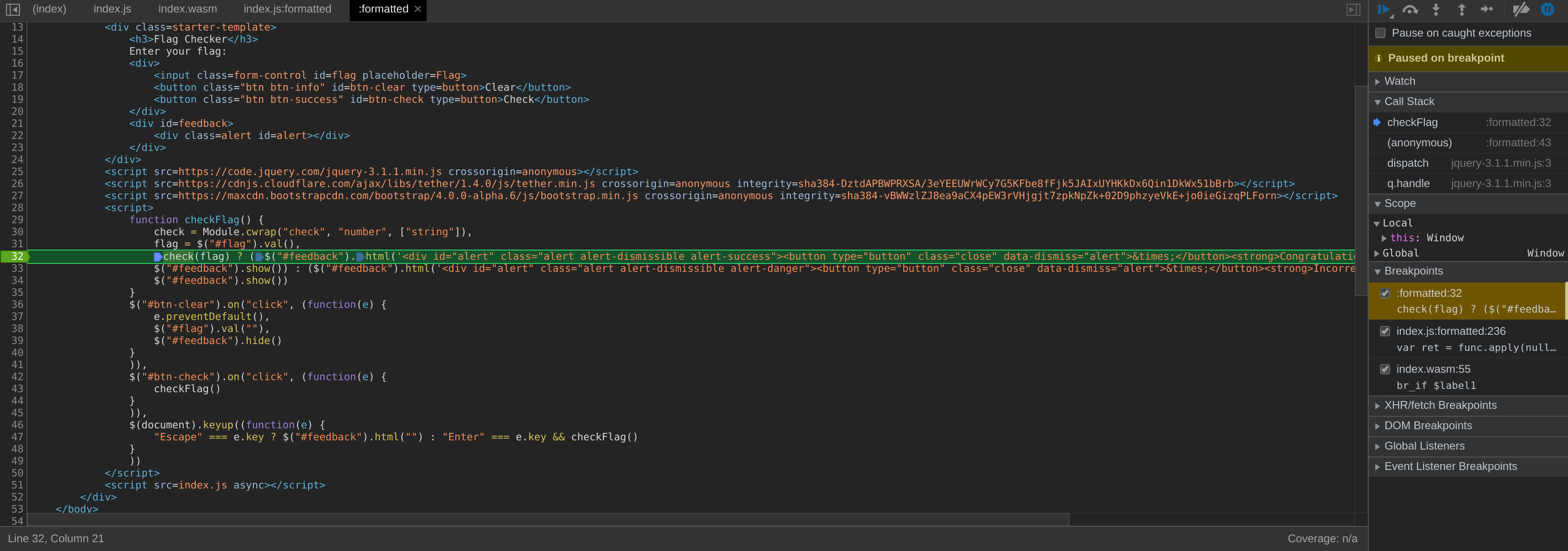
There are a lot of call, the call stack getting bigged and bigger. I only focused on the calls where my initial input, acab, was passed.
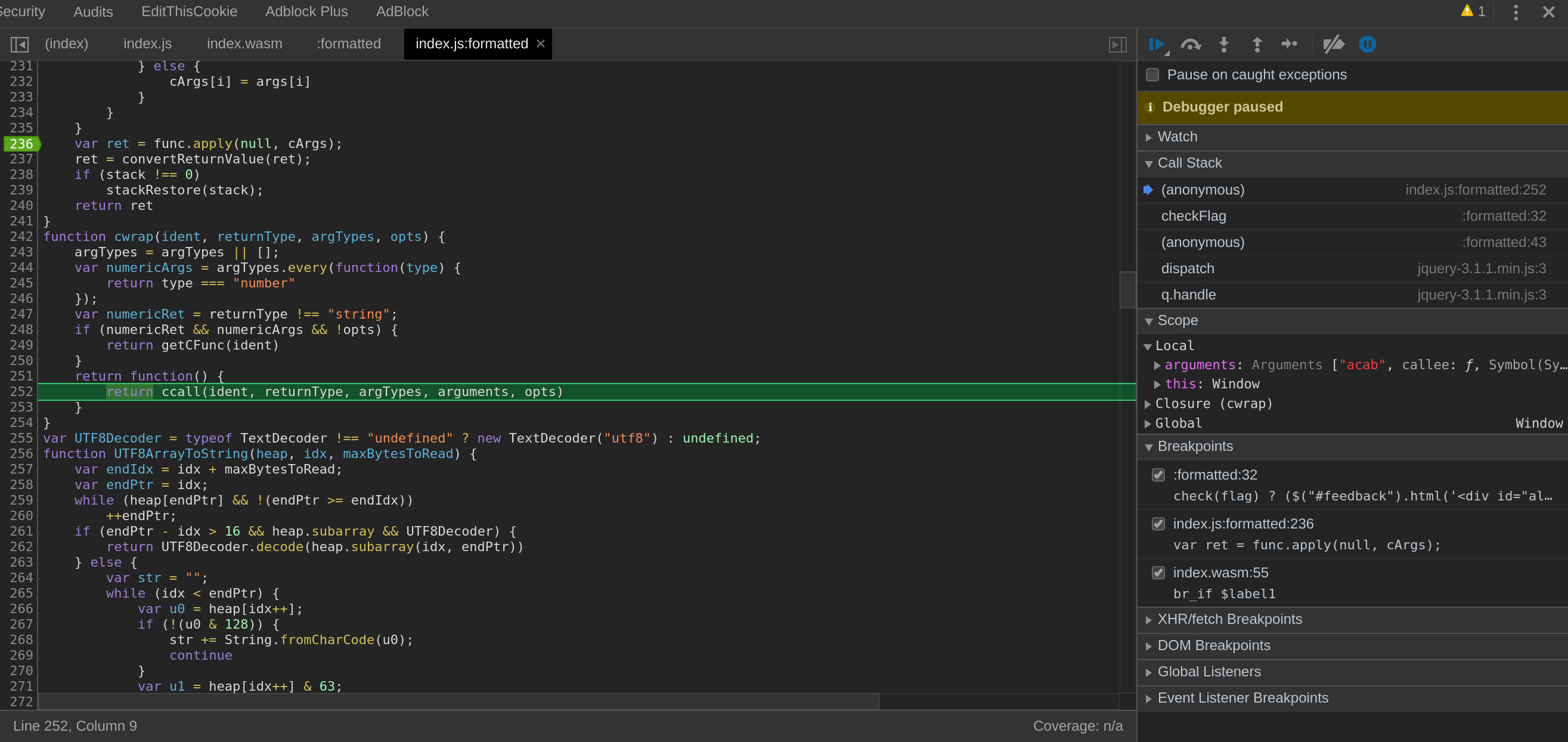
This call seems the one making the call to functions presents in the index.wasm file.
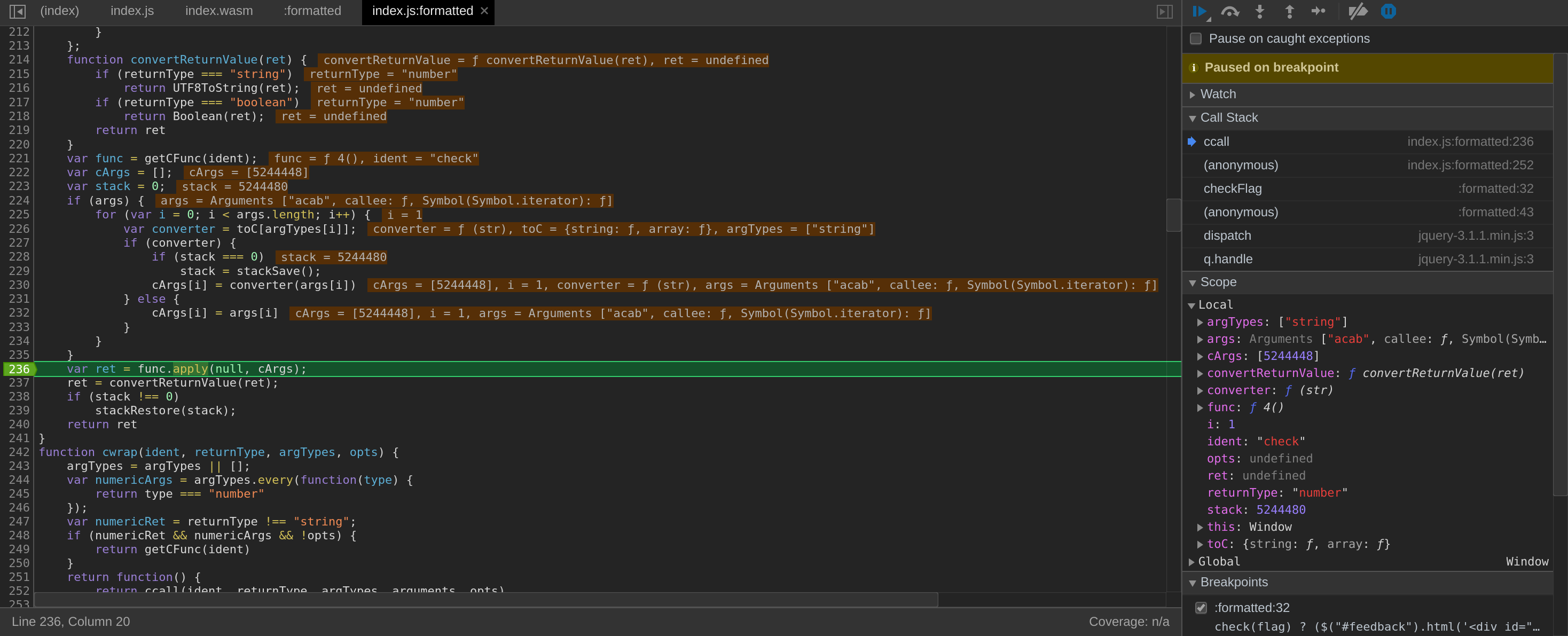
When you do a bit of reverse you can easily read IL (Intermediate Language) or diverse assembly as the logic is often the same behind. Between assemblies, at a high level, function call or logic branches are quite similar.
Here I saw a long string, a const 3 and the operation xor, while on CTF a light should turn on in your head aha. After quickly reading it before to test my idea, the code look like very small and manipulate only few locals vars with no reference to other functions so, keep it simple.
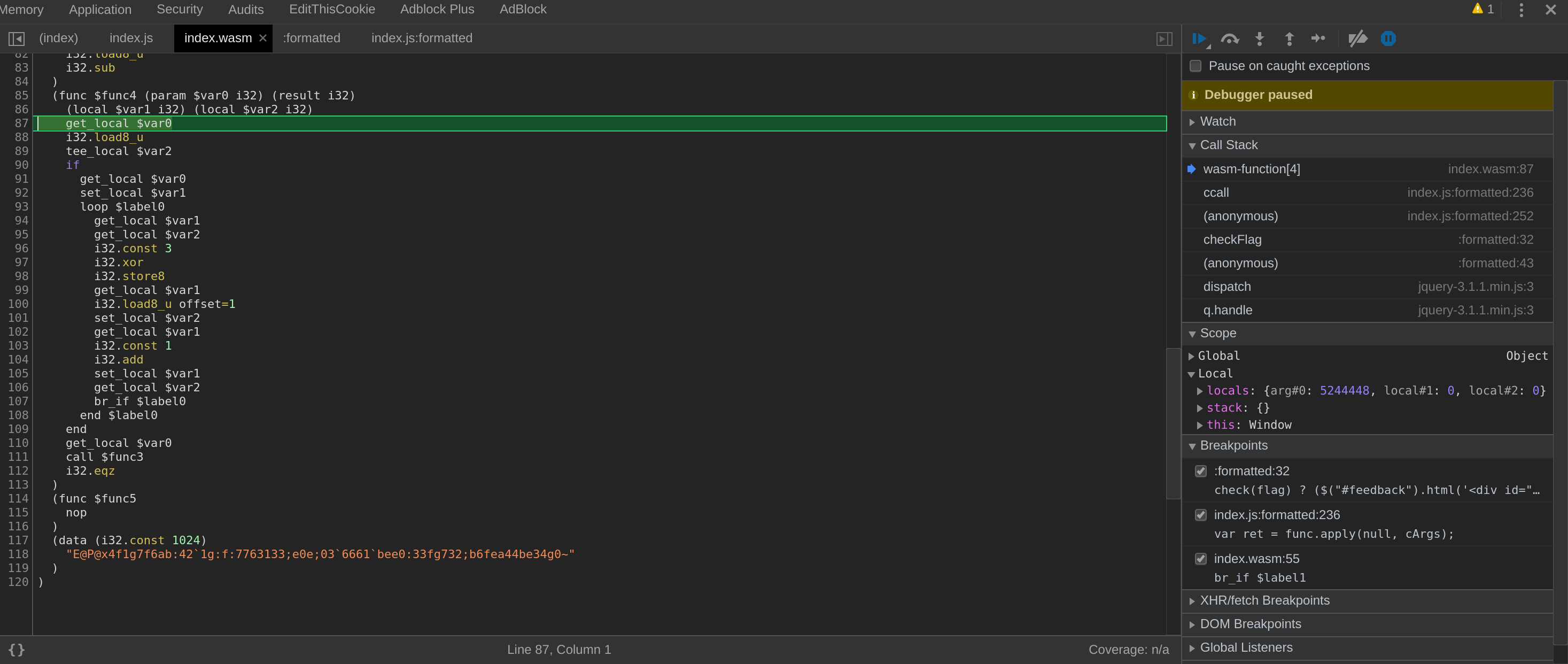
I given a try and it worked :)
Python 3.8.2 (default, Apr 8 2020, 14:31:25)
[GCC 9.3.0] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> from pwn import *
>>> xor("E@P@x4f1g7f6ab:42`1g:f:7763133;e0e;03`6661`bee0:33fg732;b6fea44be34g0~", 3)
b'FCSC{7e2d4e5ba971c2d9e944502008f3f830c5552caff3900ed4018a5efb77af07d3}'
>>> 10955
10955